CHAPTER 4: Deploying Windows 10 and Office 365 ProPlus
Welcome to Deploying Windows 10 and Office 365 ProPlus. In this chapter, we are going to cover the different ways that you can deploy Windows 10 and Office 365 ProPlus in your environment. We will start things off by covering the steps you need to take to plan for Windows 10 and Office 365 ProPlus deployments. We’ll cover hardware assessment and application compatibility assessment, along with network assessment and optimization.
Next, we’ll cover the different deployment options for Windows 10. We’ll look at things like Windows autopilot, in-place upgrades, and dynamic provisioning. We will also look at subscription activation as a means for switching from one edition of Windows 10 to another.
After covering the deployment options for Windows 10, will take a look at the different deployment options for Office 365 ProPlus. We will take a look at Configuration Manager, the office deployment tool, and manual installation from the Office 365 portal.
Once we finish working through the different Office 365 ProPlus deployment options, we’ll cover servicing channels and deployment rings.
Coming down the home stretch, we will cover updates for Office 365 ProPlus. We’ll take a look at the different update channels for Office 365 ProPlus including the Monthly Channel, the semiannual targeted channel, and the Semi-Annual Channel. In this lecture, you’ll learn how to choose the appropriate update channel for your organization and how updates are installed for Office 365 ProPlus.
Rounding things out, we’ll dive into licensing and activation in Office 365 ProPlus, where you’ll learn about licensing Office 365 ProPlus, reduced functionality mode, and how to activate Office 365 ProPlus. You’ll also learn how to manage activated installations.
Planning Deployments
When planning an enterprise deployment of Windows 10 and Office 365 ProPlus, you need to ensure that you properly assess your environments and your network. You also need to make sure that any existing hardware and applications in your environment will work with your new software.
Assessing Compatibility
Although virtually all applications that have been written in the last decade will run on Windows 10 - and virtually all add-ins and VBA macros that are based on previous versions of Office will work in the latest versions of Office - your organization should ensure that existing applications and hardware will support Windows 10 and Office 365 ProPlus before rolling them out.
To help with this process, Microsoft offers several different tools.
The Windows Analytics Upgrade Readiness Tool is provided to assess desktop, device, and application readiness. This tool provides information about application and driver compatibility, and it provides a detailed assessment of any identified issues that could prevent an upgrade. It also provides links to suggested fixes for any issues it identifies.
The Readiness Toolkit for Office Add-Ins and VBA is designed to help organizations identify compatibility issues with existing Microsoft VBA macros and add-ins. This tool scans for VBA macros in Word, Excel, PowerPoint, Access, Outlook, Project, Visio, and Publisher files.
Desktop App Assure is a new service that you can use to address issues with Windows 10 and Office 365 ProPlus application compatibility. This service comes with the Fast-Track Center Benefit for Windows 10. To get access to the Fast-Track Center Benefit for Windows 10, you must have an eligible subscription. An eligible subscription is one that includes at least 150 licenses for an eligible service or plan for your Office 365 tenant.
Before deploying Windows 10 and Office 365 ProPlus in production, Microsoft recommends that you first deploy them to a pilot group of users on a pilot group of devices across the organization. By testing your deployment with a pilot group first, you can mitigate any issues that crop up before you deploy into production.
Network Assessment and Optimization
Before deploying and managing updates for Windows 10 and Office 365 ProPlus, you need to ensure you have the necessary bandwidth to do so. The Office 365 ProPlus installation files are at least 1.6 GB in size – and this is just for the core files. Each language that you deploy will add another 250 MB.
To help deal with network bandwidth limitations, there are several built-in methods for automatically limiting bandwidth. Express Update Delivery and Binary Delta Compression both help reduce the size of your update downloads. These methods ensure that you only download the changes that have occurred between the current update and the previous update. This typically vastly minimizes the impact to your network.
There also peer-to-peer options available. These options essentially shift Windows 10 and Office 365 ProPlus traffic away from the center of your network. What this does is reduce the need for throttling. Using a peer-to-peer option allows computers to find necessary update files on other machines in the local network, instead of downloading those files from a central distribution share on the network or from the internet.
There are currently three peer-to-peer options available. These options include Branch Cache, Peer Cache, and Delivery Optimization.
Branch Cache allows you to download source files in a distributed environment without crushing your network. What Branch Cache does is retrieve the content from the main office or from hosted cloud content servers. It then caches that content at your branch office locations. Users from these locations can then access that content locally instead of accessing it over the WAN.
Peer Cache comes with Configuration Manager. It allows clients to share source files directly from other clients. Organizations will often use Peer Cache to manage the deployment of source files to users in remote locations. You can use Branch Cache and Peer Cache together in the same environment.
With Delivery Optimization, your clients can download source files from alternate sources, including other peers on the local network. This is in addition to Windows Update Servers. Delivery Optimization can be used with Windows Update, Windows Server Update Services (WSUS), Windows Update for Business, and Configuration Manager.
By assessing hardware and application compatibility, and assessing and optimizing your network, you can ensure a smooth deployment of Windows 10 and Office 365 ProPlus.
Windows 10 Deployment Options
There are actually quite a few ways to deploy Windows 10 in an organization. You can use existing tools such as InTune, Azure AD, and Configuration Manager OR you can you one of several new deployment tools and methods that are now available. These new tools and methods include Windows Autopilot, In-Place Upgrades, Dynamic Provisioning, and Subscription Activation.
With Windows Autopilot, you can customize the out of box experience (OOBE) so that you can deploy applications and settings that are preconfigured specifically for your organization. This allows you to include just the applications that your users need. Windows Autopilot is probably the easiest way to deploy new PCs that run Windows 10. It can also be used in conjunction with Configuration Manager to upgrade Windows 7 and Windows 8.1 machines to Windows 10.
Leveraging In-Place Upgrades allow you to upgrade to Windows 10 without reinstalling the OS. This method allows you to migrate applications, user data, and settings from one version of Windows to another. You can also use an in-place upgrade to update a Windows 10 machine from one release to the next.
Dynamic Provisioning allows you to create a package that you can use to quickly configure multiple devices, even those that have no network connectivity. Using Windows Configuration Designer, you can create provisioning packages and install them over the network, or even from a USB drive. They can also be installed in NFC tags or barcodes.
Using Subscription Activation, you can use subscriptions to switch from one edition of Windows 10 to another. An example of this would be a scenario where you need to switch a user from Windows 10 Pro to Windows 10 Enterprise. In this scenario, if a licensed user signs into the Windows 10 device, assuming the user has a Windows 10 E3 or E5 license, the operating system automatically changes from Windows 10 Pro to Windows 10 Enterprise. This unlocks the Windows 10 Enterprise features. I should mention that if the associated E3 or E5 license expires, the Windows 10 device simply reverts back to the Windows 10 Pro addition. You are, however, offered a grace period of up to 90 days before it reverts back.
So, as you can see there are several ways to deploy Windows 10.
Deployment Options for Office 365 ProPlus
There are several ways to deploy Office 365 ProPlus. Let’s take a look at the options that are available.
You can use Configuration Manager, the Office Deployment Tool, and Microsoft InTune to perform Office 365 ProPlus deployments. You can, of course, also install directly from the Office 365 portal.
Configuration Manager is a good choice for enterprises that already leverage a solution to deploy and manage their existing software. The Office Deployment Tool is a good choice for organizations who need to manage their Office 365 ProPlus deployment, but do not have Configuration Manager deployed. Organizations that wish to deploy and manage Office 365 ProPlus directly from the cloud should consider Microsoft InTune. However, the easiest approach to deploying Office 365 ProPlus is to just allow your users to install it directly from the Office 365 Portal. The caveat to this solution, though, is that it provides far less control over the deployment process.
When you deploy Office 365 ProPlus using the Office Deployment Tool or through Configuration Manager, you’ll typically create configuration files using the Office Customization Tool. These configuration files are then used to define the configuration of Office. This process provides you with more control over your installations. There are also similar options available when you use InTune to deploy Office 365 ProPlus.
I should mention here, that depending on how you decide to deploy Office 365 ProPlus, you can choose to deploy directly from the cloud or you can download Office to local storage on your network, where you can then deploy from. Microsoft, however, recommends that you deploy Office directly from the cloud because it minimizes administrative overhead. When deployed in this fashion, Office 365 ProPlus is installed on your client devices right from the Office Content Delivery Network. If you find that your internet bandwidth can’t support installations directly from the cloud, you can use Configuration Manager to manage your deployments and updates that can be pulled from a local network location.
The deployment option you choose will be largely dependent on your network infrastructure, your user base, and your corporate policies.
Windows-as-a-Service
Under the Windows-as-a-Service model, Microsoft has simplified the OS build and deployment process. Instead of providing major OS revisions every few years, with service packs released between those revisions, Windows updates are now treated more like ongoing maintenance tasks. This means that Windows will now receive updates and revisions on a more frequent basis. These updates and revisions are also applied with less disruption.
These new updates fall into two different buckets. These buckets include Feature Updates and Quality Updates. Feature Updates are updates that add new functionality. They are released twice a year and can be deployed using existing management tools. Feature Updates are typically smaller because they are more frequent. Because they are smaller, the impact to organizations when deploying them is reduced.
Quality Updates are security updates and fixes. These updates are typically issued once a month. More specifically, the second Tuesday of each month, otherwise known as Patch Tuesday. When a cumulative update is released on Patch Tuesday, it includes all previous updates. This makes it easier to ensure that devices are fully up to date.
You can use deployment rings and servicing channels to control how updates are applied - and when.
Servicing Channels
There are three servicing channels offered by Windows-as-a-Service. Each channel receives new feature updates on a different schedule. These channels include the Semi-Annual Channel, the Long-Term Servicing Channel, and Windows Insider. The purpose of these servicing channels is to provide organizations with a way to control the frequency at which they deploy Windows 10 features.
Deployment Rings
Deployment rings are similar to machine groups that you may have used previously to manage updates for earlier versions of Windows in WSUS. There used to gradually deploy Windows 10. You can use deployment rings to group devices together and to ensure those devices receive their updates through the same servicing channels.
You can use the same management tools to deploy servicing channel updates that you used in earlier versions of Windows. For example, you can use the Windows Insider program to allow users to familiarize themselves with Windows features before they are released to the larger population of users within the organization. This allows organizations to get a look at early builds and to test them before they are released to the general public.
You can use the Semi-Annual Channel to receive updates as soon as Microsoft publishes them. Feature updates go out to the Semi-Annual Channel Once in the spring and once in the fall.
You can also use the Long-Term Servicing Channel to deploy updates to your organization. The Long-Term Servicing Channel is for computers and other devices that essentially perform a single task or several specialized tasks. For these types of computers and devices, the Long-Term Servicing Channel prevents them from receiving feature updates. However, quality updates are not affected. I should point out that the Long-Term Servicing Channel is only available in the Windows 10 Enterprise LTSC edition. Feature updates are released to LTSC about once every three years.
A typical deployment ring strategy might consist of four rings. For example, the first ring may be a preview ring that leverages the Windows Insider Program. This ring would be reserved for a small group of devices that you wish to use for testing. The next ring would be the targeted ring, which leverages the Targeted Semi-Annual Channel. You would use this ring to evaluate important updates before you deploy them to other devices in your environment. The next ring would be the production ring. This ring would leverage the Semi-Annual Channel and would be used to deploy updates to production machines. A fourth ring might be a critical ring. This critical ring would leverage the Semi-Annual Channel as well, but it would be reserved for machines that are critical, and which are only updated after thorough testing throughout the rest of your organization.
Ring strategies like the one in this example allow organizations to control how updates are deployed to all of their devices.
Windows-as-a-Service, when leveraged properly, is essentially an ongoing process that you use to handle Windows updates in an organization. The servicing models that are available for managing Windows-as-a-Service updates include Windows Update (or standalone), Windows Update for Business, WSUS, and System Center Configuration Manager (SCCM).
Windows Update offers limited control over feature updates. Devices are typically manually configured to use the Semi-Annual Channel. An organization that uses Windows Update can specify when updates get installed and to what devices. I should also mention that the updates do not even have to come from an on-prem server.
Windows Update for Business provides control over update deferments while also allowing for centralized management through group policy. You can use Windows Update for Business to defer updates for up to a year. Devices that are updated using Windows Update for Business need to be updated periodically and monitored using one system.
Windows Server Update Services, or WSUS, allows for significant control over Windows updates. This tool, which is native to the Windows Server OS, allows organizations to not only defer updates, but to also add an approval layer for updates that allows organizations to specify groups of computers that should receive updates.
System Center Configuration Manager offers the most control and is the most cost-effective option to service Windows-as-a-Service. Updates can be deferred and approved by IT staff, and there are also multiple options for targeting and bandwidth management. System Center Configuration Manager allows for consistent scheduling of updates across all devices within the enterprise. I should point out, however, that application deployments and operating system updates must originate from an on-prem server when using system Center Configuration Manager.
So which servicing option, should you choose? Well, the servicing option that you choose will be largely governed by the resources you have available to you, your IT staff, and the knowledge of that IT staff. If you already use. System Center Configuration Manager to manage your Windows updates, it probably makes sense to continue using it. However, if you are already using a solution like WSUS, it probably makes sense to continue using WSUS. Your environment and your staff will ultimately determine which solution is right for you.
Office 365 ProPlus Updates
There are several types of updates that are available for Office 365 ProPlus. Let’s take a look at these types of updates and figured out how to choose the appropriate update channel for your organization.
Because Microsoft provides new features for Office 365 applications pretty regularly, it’s important that you keep it updated. Microsoft offers multiple update channels that you can use to keep Office 365 ProPlus updated. These channels are used to control how often Office 365 ProPlus receives feature updates.
The three primary update channels that are available for Office 365 ProPlus include the Monthly Channel, the Targeted Semi-Annual Channel, and the Semi-Annual Channel. The Monthly Channel, as you would expect, receives feature updates roughly every month. The Targeted Semi-Annual Channel receives feature updates in March and in September. Organizations will often use this channel for its pilot users and for application compatibility testing. The Semi-Annual Channel receives feature updates twice a year, once in January and again in July.
The feature updates that are released in the Semi-Annual Channel will generally have already been released through the Monthly Channel in prior months. I should note that the Semi-Annual Channel is the default update channel for Office 365 ProPlus.
Microsoft also provides additional updates for each channel as needed. These include Security Updates and Quality Updates. While Security Updates are often released on patch Tuesday, which is the second Tuesday of every month, they can be released at other times when needed. Quality Updates are non-security updates which are also released on patch Tuesday.
Choosing the Right Update Channel
Organizations obviously have different needs - and these needs will determine which update channels are needed. For example, an organization might leverage the Semi-Annual Channel if it uses business applications, add-ins, and macros that must be tested to ensure they work with an updated version of Office 365 ProPlus.
However, an organization that wants its users to have access to the latest Office 365 ProPlus features as soon as they become available might want to leverage the Monthly Channel, assuming there is no need for any kind of application compatibility testing.
It’s important to note that an organization can leverage different update channels for different users. Not all users need to be on the same channel.
Installing Updates for Office 365 ProPlus
When an Office 365 ProPlus update occurs, all updates for the specific channel are installed at the same time. For example, you won’t get a separate download for Security Updates, a separate download for Quality Updates, etc. They are all installed at the same time. I should also mention that updates are cumulative. This means that the latest update will include all previously released feature, security, and quality updates for the specific channel.
Office 365 ProPlus goes out and checks for updates on a regular basis. These updates are then downloaded and installed automatically. Although users can continue using their office applications while uploads are being downloaded, once the actual update installation begins, those users will be prompted to save their work and to close their apps to allow the installation of the downloaded updates.
Office 365 Licensing and Activation
Before you can deploy Office 365 ProPlus to your users, you first need to assign licenses to them. Once you’ve assigned licenses to your users, they can begin installing the software. Once licensed, each user can install Office 365 ProPlus on up to five different computers or devices. Because each installation is activated and kept activated automatically, you don’t even have to keep track of product keys. You also don’t have to worry about dealing with KMS or MAK services. What you do have to do, however, is ensure that your users connect to the internet at least once every 30 days so their licenses can be kept activated by the Office licensing service.
Licensing Office 365
Assigning an Office 365 ProPlus license to a user is as simple as checking a box on the licensing page for the users account. Once you’ve assigned licenses to your users, they can install office right from the Office 365 portal. You can also deploy Office to your end users from a shared location on your local network. Users cannot install Office from the Office 365 portal until they have been assigned a license.
Reduced Functionality Mode
If you remove a user’s Office 365 ProPlus license, any existing installations of Office 365 ProPlus for that user will go into what is called Reduced Functionality Mode. Deactivating a user’s Office 365 ProPlus license for a specific device will also cause Office 365 ProPlus to go into Reduced Functionality Mode, but only on that device.
An Office 365 ProPlus installation that has gone into Reduced Functionality Mode will remain installed on the computer; however, the user will only be able to view and print documents. They will not be able to edit documents nor create new documents.
I should also point out that every time the unlicensed user runs Office 365 ProPlus, that user will be prompted to sign in and activate the software.
Activating Office 365 ProPlus
When Office 365 ProPlus is installed, it communicates back to the Office Licensing Service and the Activation and Validation Service. It does this so it can obtain and activate a product key. Whenever a user logs into his computer, the computer will connect to the Activation and Validation service. This is done in order to verify the license status of the software and to extend the product key.
Office will remain fully functional as long as the computer connects to the internet at least once every 30 days. Office will enter Reduced Functionality Mode if a computer goes off-line for more than 30 days. Once the computer connects back to the internet, the Activation and Validation Service will automatically reactivate the installation and it will become fully functional again.
Managing Activated Installations
As I mentioned previously, an Office 365 ProPlus license allows a user to install Office on up to five different computers. However, if that user tries to install Office 365 Pro on sixth computer, the user will first need to deactivate one of the existing five installations. This causes the installation that is deactivated to go into Reduced Functionality Mode.
What You’ve Learned
Congratulations! You’ve reached the end of Deploying Windows 10 and Office 365 ProPlus. Let’s review what you’ve learned.
Throughout this chapter, we covered the different ways that you can deploy Windows 10 and Office 365 ProPlus in your environment. We started things off by covering the steps you need to take to plan for Windows 10 and Office 365 ProPlus deployments. We covered hardware assessment and application compatibility assessment, along with network assessment and optimization.
Next, we covered the different deployment options for Windows 10. We looked at things like Windows Autopilot, In-Place Upgrades, and Dynamic Provisioning. We also looked at Subscription Activation as a means for switching from one edition of Windows 10 to another.
After covering the deployment options for Windows 10, we reviewed the different deployment options for Office 365 ProPlus. We looked at Configuration Manager, the Office Deployment Tool, and Manual Installation from the Office 365 portal.
Once we finished working through the different Office 365 ProPlus deployment options, we dove into the Windows-as-a-Service model, where we covered servicing channels and deployment rings.
Coming down the home stretch, you learned about updates for Office 365 ProPlus. You learned about the different update channels for Office 365 ProPlus including the Monthly Channel, the Semi-Annual Targeted Channel, and the Semi-Annual Channel. You also learned how to choose the appropriate update channel for your organization and how updates are installed for Office 365 ProPlus.
Rounding things out we dove into licensing and activation in Office 365 ProPlus, where you learned about licensing Office 365 ProPlus, Reduced Functionality Mode, and how to activate Office 365 ProPlus. You also learned how to manage activated installations.
At this point, you should have a good idea of what all goes into planning for and deploying Windows 10 and Office 365 ProPlus.
CHAPTER 7: Security Fundamentals
 Welcome to Security Fundamentals. In this chapter, we are going to cover a few different fundamental security topics.
Welcome to Security Fundamentals. In this chapter, we are going to cover a few different fundamental security topics.
We will start things off by covering the 4 key security pillars of protection. We'll look at identity and access management, threat protection, information protection, and security management.
Next, we’ll cover key identity and access management concepts.
After covering identity and access management concepts, we'll look at threat protection concepts, where you'll learn about the ways you can protect your network against threats from devices and against network threats. Rounding out the chapter, you'll learn about information protection concepts and security management concepts.
Pillars of Protection
Any respectable security design will provide defense in depth. Defense in depth is a security concept that involves the use of several different layers of security to protect data. Defense in depth is important because if a hacker is able to compromise one layer of defense, there are still several others to offer protection. An example of defense in depth in a network environment would be in architecture that features an external firewall, a DMZ, an internal firewall, and then firewalls that are configured on each computer.
Because no single security solution can ensure data security at all times, organizations should take this layered defense in depth approach to protect themselves. Protecting data on computers or servers, for example, may include drive encryption, file and folder permissions, and maybe even rights management.
Microsoft takes a holistic approach to security. In doing so, it helps organizations protect their identities, their data, their applications, and their devices, whether they reside on-prem, in the cloud, or are mobile.
The key pillars that are foundational to the security of every computer system include identity and access management, threat protection, information protection, and security management.
Identity and Access Management
The identity piece of identity and access is used to identify users before they are authorized to access IT resources. Users are typically identified via user accounts, which are assigned the necessary levels of access for particular resources. Each user in an organization may actually have several different user accounts. These accounts can include local login accounts, Active Directory accounts, Azure Active Directory accounts, or Microsoft accounts.
A local user account is specific to a local Windows 10 device only. A local account on one computer will not allow access to resources on another computer. Devices can also have local accounts. For example, all Windows 10 computers have local accounts, but those local accounts are usually not used interactively.
Because most organizations use traditional Active Directory forests to manage their users and computers, domain accounts are another prominent type of user account. These types of accounts are used to authenticate users when they access domain joined devices.
Azure AD accounts are user accounts that are stored in Azure Active Directory. These accounts are generally used to access resources and services that are hosted in the cloud. Office 365 immediately comes to mind. Organizations that use both a traditional on-prem Active Directory and an Azure Active Directory can integrate the two via synchronization with Azure AD Connect.
Microsoft accounts include an email address and password. These accounts are used to sign into many different services and can be used regardless of the user location or organization that a user is a member of. Users that have signed into services like Xbox live or Outlook.com, among others, already have a Microsoft account.
Microsoft accounts can also be used to authenticate with Azure AD.
There are of course many other types of accounts, including social accounts, like Facebook accounts and Twitter accounts.
Since user accounts are the primary way of determining who a user is it’s critical that those accounts be protected and it’s critical that the identity verification process is protected as well. This is referred to as identity protection.
Microsoft 365 offers several features that can be used to identify compromised user accounts. It can, for example, detect new or unusual sign in locations that often indicate an account has been compromised. You can then take action based on these unexpected changes.
Threat Protection
Every time a device connects to your infrastructure, it has the potential to bring with it security risks. For example, if a particular device does not have a properly configured firewall running, it is a threat to the network every time it connects - especially if the device often connects to unsecured public networks when it’s not on the corporate LAN.
A device without antivirus or antimalware protection is obviously a threat because of its risk of being infected with malware. When a device like this attaches to the network, such malware can then be spread to other devices within the organization.
Unpatched operating systems and applications are additional threats to the organization that originate from devices. Because malicious software often takes advantage of unpatched systems, these types of systems and devices can serve as an opening to the corporate LAN.
Poor passwords and poor physical security are also risks that devices introduce to the corporate network. A phone or a device that is protected with an easy to guess PIN or password is a risk because if it is stolen, the data on that device is readily accessible. As far as physical security goes, many users will often leave their devices unattended in public places like airports and Internet cafés. In such scenarios, not only can a device be stolen, but it can also be tampered with.
Many of these risks to device security can be mitigated through end-user education on how to properly secure devices with complex passwords, pins, and biometric protection. That said, education only goes so far. As a result, in order to properly secure your organization’s IT infrastructure, you need to be able to enforce corporate security settings on these devices, including those that are owned by the users. By restricting access to corporate resources to only those devices that adhere to such policies, you can better protect your environment.
Network security is a whole other ball of wax. While there are many different types of attacks that threaten a network, most can be mitigated with some proper network access planning.
To protect your network, you need to take a holistic approach. Every possible threat must be identified and there needs to be a plan for mitigation. For example, there should be a rigorous form of authentication in place for devices that wish to connect to the network. Another way to protect against network sourced threats is to only allow guest users to access the Internet from guest networks, and not from the corporate network.
Information Protection Concepts
To properly protect organizational data, that data needs to be protected both at rest and in transit.
Data at rest is data that is stored somewhere like a file server or on a hard drive. Data at rest can also be stored on a USB flash drive or even in mailboxes. The security risks that are associated with each of these storage locations differs significantly. Data on a thumb drive, for example, can easily be lost because thumb drives are easy to misplace. Because laptops are usually targets for theft, data stored on laptops can disappear rather quickly as well. Because hackers know that organizational file servers often contain critical data, such file servers are often targeted.
Each scenario presents different challenges. That being the case, it’s important to understand which data protection solutions are the right ones to use. Some solutions that can be used to protect data at rest include drive encryption, rights management software, antimalware, and even enhanced network security.
Data in transit is data moving between devices. An example of data in transit would be a user accessing files on a file server or when a user reads his email on his cell phone. Authentication and encryption are used to ensure the safety of data that is in transit from one device to another.
So, the key takeaway here is that there are two information protection concepts to keep in mind. You must protect data at rest, and you must protect data in transit.
Security Management
Security management actually is a combination of the first three concepts that we’ve discussed. It brings together identity and access management, threat protection, and information protection. In order to address these other pillars of security. You need an effective security management process.
Because security management is both proactive and reactive, it’s important to implement solutions that address both sides of the coin. Taking a proactive security management position will often require you to deploy certain types of authentication, like complex passwords and MFA, to meet perceived threats.
Reactive management will require you to deploy tools that you can use to identify security threats that are happening right now. This means you should deploy monitoring tools that cannot only identify active threats, but that can also help you take the correct mitigation steps.
By taking the right security management tact, you can ensure that you are properly addressing the three other key pillars of security.
What You’ve Learned
Congratulations! You have come to the end of Security Fundamentals! Let's review what you've learned.
We kicked things off by covering the 4 key security pillars of protection. We looked include identity and access management, threat protection, information protection, and security management.
Next, we covered key identity and access management concepts.
After covering identity and access management concepts, we looked at threat protection concepts, where you learned about the ways you can protect your network against threats from devices and against network threats.
Rounding things out, you learned about information protection concepts and security management concepts.
MS-900 Exam-Prep Guide: Meet the Author
 Thomas Mitchell is a 25+ year veteran of the IT Industry. After spending the last two decades as a Senior Engineer and Solutions Architect for several organizations, including national, international, and global enterprises, Tom now focuses on teaching and providing freelance IT consulting and solution design services for organizations around the world.
Thomas Mitchell is a 25+ year veteran of the IT Industry. After spending the last two decades as a Senior Engineer and Solutions Architect for several organizations, including national, international, and global enterprises, Tom now focuses on teaching and providing freelance IT consulting and solution design services for organizations around the world.
Tom's specialties include Microsoft Azure, Microsoft Active Directory, Microsoft 365, and Messaging (Exchange & Exchange Online).
Tom is the founder of labITout.com, a website that IT professionals use to learn how to deploy real-world IT solutions through guided labs. Tom has also trained over 40,000 students in over 200 countries through the Udemy platform.
Some of Tom’s highest rated courses include:
- MS-900 Exam Prep: Microsoft 365 Fundamentals Course
- AZ-900 Azure Exam Prep: Microsoft Azure Fundamentals
- Deploying and Managing Azure Virtual Machines
- Getting Started with Okta
- Extending On-Prem Active Directory into Microsoft Azure
- AZ-103 Exam Prep: Microsoft Azure Administrator
- Creating and Managing Azure Virtual Machines with PowerShell
- How to Perform an Express Migration from Exchange to O365
There are also several more highly rated courses that Tom teaches on Udemy as well.
CHAPTER 10: Microsoft 365 Pricing and Support
 Welcome to Microsoft 365 Pricing and Support. In this chapter, we are going to review the Microsoft 365 subscription options that are available, how to manage Microsoft 365 licenses, how to manage billing, and how to get Microsoft 365 support.
Welcome to Microsoft 365 Pricing and Support. In this chapter, we are going to review the Microsoft 365 subscription options that are available, how to manage Microsoft 365 licenses, how to manage billing, and how to get Microsoft 365 support.
Microsoft 365 Subscription Options
As you’ve learned throughout this book, Microsoft 365 is a complete software-as-a-service solution that includes Microsoft Office 365, Windows 10, and Enterprise Mobility + Security, all bundled into a single subscription. Because every business is different and every business has different requirements, Microsoft offers several different subscriptions and plans to accommodate those differing requirements. These subscriptions include Microsoft 365 Enterprise, Microsoft 365 Business, Microsoft 365 Education, and Microsoft 365 for First Line Workers.
Microsoft 365 Enterprise offers enterprise class services to organizations that require robust threat protection, security, compliance, and analytics features. Under the Microsoft 365 Enterprise umbrella, you’ll find two different plans. They include the E3 plan and the E5 plan.
| Feature | E3 | E5 |
| Windows 10 Enterprise | x | x |
| Word, Excel, PowerPoint, OneNote, Access, Exchange, Outlook, Teams | x | x |
| StaffHub, PowerApps, Flow, Skype for Business, SharePoint, Yammer | x | x |
| Advanced Threat Analytics, Windows Defender Antivirus, Device Guard | x | x |
| Azure Active Directory Plan 1, Windows Hello, Credential Guard, Direct access | x | x |
| Intune, Windows Autopilot, Fine Tuned User Experience, Windows Analytics Device Health | x | x |
| Windows Information Protection, Bitlocker & Azure Information Protection P1 | x | x |
| Office 365 Data Loss Preventions, Delve | x | x |
| Power BI Pro, MyAnalytics, Audio conferencing, Phone System | x | |
| Windows Defender ATP, Office 365 ATP, Office 365 Threat Intelligence | x | |
| Azure Active Directory Plan 2 | x | |
| Azure Information Protection P2, Microsoft Cloud App Security, Office 365 Cloud App Security | x | |
| Advanced eDiscovery, Customer Lockbox, Advanced Data Governance | x | |
The table above highlights the features that are included in each plan. As you can see, the E5 plan includes all of the same features as the E3 plan, plus more advanced threat protection, security, and collaboration tools.
You can purchase Microsoft 365 Enterprise licenses through a cloud solution provider, or CSP, or you can purchase them through an Enterprise Agreement subscription from Microsoft.
Microsoft 365 Business is well suited for smaller and medium-sized organizations. Like its older brother, Microsoft 365 Enterprise, Microsoft 365 Business offers the same full set of office 365 productivity tools. While it does include many security and device management features, Microsoft 365 Business does NOT include many of the advanced information protection, compliance, or analytics tools that are available in the enterprise plan. Microsoft 365 Business is designed for organizations with 300 users or fewer. If your organization requires more than 300 licenses, you will need to subscribe to an enterprise plan instead.
Microsoft 365 Education, as you can probably gather from its name, is intended for educational organizations. Such organizations can obtain academic licenses that can be tailored to fit their specific needs.
Microsoft 365 for First Line Workers is referred to as the Microsoft 365 F1 Subscription. This plan is intended for first line workers, such as customer service reps, support engineers, and service professionals.
While the Microsoft 365 F1 subscription is similar in many ways to the Microsoft 365 E3 subscription, the F1 plan is designed in a way that better fits the need of first line workers. For example, since first line workers don’t typically use virtual machines, the Microsoft 365 F1 subscription includes Windows 10 E3, but doesn’t offer virtualization rights. I should also note that Microsoft 365 F1 is far less expensive than the Microsoft 365 E1 and E3 enterprise plans.
So, the key takeaway here is that Microsoft 365 Enterprise is designed for large organizations. Microsoft 365 Business is designed for small and medium-sized businesses. Microsoft 365 Education is for educational organizations and the Microsoft 365 F1 Subscription is designed for first line workers.
Managing Microsoft 365 Licenses
When you purchase a Microsoft 365 subscription, you tell Microsoft how many licenses you need, based on the number of people in your organization. When it comes time to create user accounts and to assign licenses to your users, you use the Microsoft 365 admin center. As new people come on, you use the admin center to assign licenses to them. As people leave, you can remove their licenses and reassign them to other people within the organization.
You can also manage expired licenses from the Microsoft 365 admin center. Licenses expire when you don’t renew them or if your bill is past due. When a license expires, the user with that expired license will have limited use of their Microsoft 365 products. To regain full functionality, you would need to either renew the license or assign a new, active license.
The admin center is also where you enable and disable features like Exchange Online and Microsoft Teams. These features are enabled and disabled using a toggle switch or checkbox within each license for each user. This same process is used to enable and disable many other services and tools within a user’s license. I should note, however, that deactivating individual features, or even all features for a specific user, does not free up the license itself. These individual controls simply manage which features are available to the user within that assigned license.
Admin Roles
There are various admin roles that are available within Microsoft 365. Each role can perform different licensing actions. The roles include the Global Administrator, the Billing Administrator, and the License Administrator.
The Global Administrator has access to all admin features in the Office 365 suite of services. The person that signs up to buy Office 365 automatically becomes the Global Admin. It’s also important to note that Global Admins are the only ones who can assign other admin roles, and they are the only ones that can manage the accounts of other Global Admins.
The Billing Administrator is responsible for making purchases, managing subscriptions, and managing support tickets. This role also monitors service health.
The License Administrator, as you may have guessed, is responsible for adding, removing, and updating license assignments for users and groups. This role does not offer the ability to purchase or manage subscriptions, nor does it offer the ability to create or manage users and groups. It can, however, manage the usage location for users because that is relevant to the licensing.
Billing and Support in Microsoft 365
Billing management is another task that is handled from the Microsoft 365 admin center. As you might expect, the options that are available, as well as pricing, will depend on the specific subscription and the number of users that are licensed. That said, each service has a set price that’s usually charged on a per user per month basis.
You can use the Microsoft 365 admin center to review and modify all billing aspects of your subscription. You can view the current number of purchased licenses and you can see how many of those licenses have been assigned to users. You can also view any current charges that are due on your account as well as the payment method and frequency that are on file. The frequency can be monthly or annual.
The Microsoft admin center is also used to specify a list of email addresses that should receive automated billing notifications and renewal reminders that are associated with the Microsoft 365 subscription.
When it comes to support in Microsoft 365, you have several options available. The specific details of which support options you have available to you are dependent on your specific situation. That said, let’s take a look at the different ways you can get support for Microsoft 365.
Fast-Track provides you with direct access to Microsoft 365 planning materials and to dedicated Microsoft fast-track project managers and engineers. These resources are there to help you deploy a Microsoft 365.
The O365 Assistant is an automated assistant bot that can be found in the Microsoft 365 admin center. The O365 assistant is designed to help you find answers to common support questions.
Premier Support is another option available to Microsoft 365 subscribers. The Microsoft Premier support services option is perfect for large and global enterprises with critical dependence on Microsoft products, including Microsoft 365 and Microsoft Azure. Organizations that are Premier Support members are assigned dedicated technical account managers and have additional benefits like on-site support and even advisory services.
Cloud Service Provider Tier 1 Support is provided to organizations that have purchased their Microsoft 365 subscription through a certified Tier-1 cloud solution provider, or CSP. The CSP, in this case, is the first point of contact for all service-related issues. The CSP will escalate issues that it can’t resolve to Microsoft.
Telephone Support is also available for some Microsoft 365 components.
Some other ways to get support for Microsoft 365 are the use of forums and communities. The Microsoft 365 Tech Community, for example, allows you to connect with and collaborate with other customers and to share your experiences, problems, and solutions.
The Microsoft 365 Support Forums are official Microsoft support forums that you can use to ask questions and to get answers from both Microsoft and community members. Some of the more popular Microsoft support forums include the Azure forums, the Windows forums, and the Office forms.
So, as you can see billing and support are never more than a mouse click away.
What You’ve Learned
Congratulations! You’ve reached the end of Microsoft 365 Pricing and Support. Let’s review what you’ve learned.
In this chapter, we reviewed the various Microsoft 365 subscription options that are available and how to manage Microsoft 365 licenses. We also covered billing management and the various Microsoft 365 support options that are available.
CHAPTER 9: Compliance in Microsoft 365
 Welcome to Compliance in Microsoft 365. In this chapter, we are going to review a few key Microsoft 365 compliance tools.
Welcome to Compliance in Microsoft 365. In this chapter, we are going to review a few key Microsoft 365 compliance tools.
We will start things off by covering the Service Trust Portal and Compliance Manager. You'll learn what they are, how to access them, and what features they offer. We will then look at Compliance Center, where you’ll learn about what information it provides and how to access it.
Service Trust Portal and Compliance Manager
The Service Trust Portal and Compliance Manager are used for assessing compliance risk, protecting and governing information, and responding to regulatory requests.
Service Trust Portal
The Service Trust Portal is a web portal that provides all kinds of content and tools that pertain to Microsoft security, privacy, and compliance practices. The Service Trust Portal also features third-party audits of many of Microsoft’s online services, along with information on how Microsoft’s services can help you maintain and track compliance with laws, regulations, and other standards.
For example, the Service Trust Portal offers information on ISO compliance, service organization controls, and information on NIST compliance. You’ll also find information on GDPR and FedRAMP as well.
Compliance tools that you will find on the Service Trust Portal include Compliance Manager, Trust Documents, Regional Compliance, and Privacy. Compliance Manager is a dashboard that you can use to track standards, regulations, and assessments; while the Trust Documents area includes audit reports and other data protection information as it relates to Microsoft services. Regional Compliance information includes compliance information that is specific to your region, and the Privacy information that is available includes information about the capabilities of Microsoft services that can be used to address GDPR requirements.
The Service Trust Portal can be accessed by visiting this URL.
Compliance Manager
Compliance Manager is used to meet compliance obligations, such as GDPR, ISO, NIST, and HIPAA.
The three main capabilities that Compliance Manager provides include ongoing risk assessment, actionable insights, and simplified compliance. The ongoing risk assessment is essentially a summary of your organization’s compliance posture when measured against regulatory requirements that apply to your business. This information is provided in the context of using Microsoft cloud services. The compliance score that is provided on the dashboard can be used to help make compliance decisions.
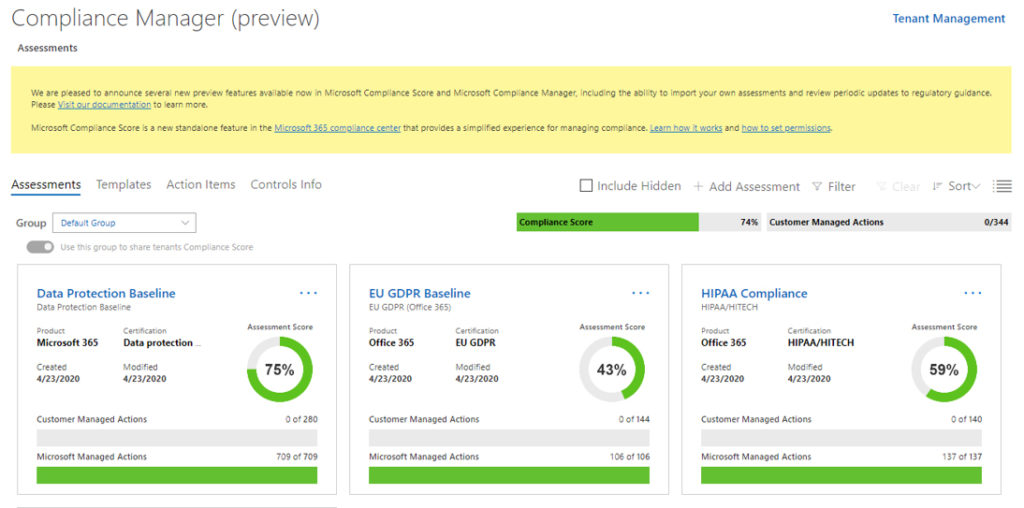
Actionable insights offer information on the compliance responsibilities that are split between the customer and Microsoft. For components and services that are managed by the customer, the dashboard will present recommendations and instructions for implementing them.
To ensure simplified compliance, Compliance Manager offers built-in collaboration tools that can be used, to assign tasks to teams within your organization. You can also create audit ready reports that link out to evidence that you collect to demonstrate your compliance.
Microsoft Compliance Center
The Compliance Center is essentially a dashboard that’s designed for compliance, privacy, and risk management staff. You use this dashboard to assess your organization’s compliance risks through its integration with compliance manager. You also use Compliance Center to protect your data and to govern it. It’s the place to go if you want or need to respond to regulatory requests and to access other compliance and privacy solutions.
Due to its integration with Compliance Manager, you can use Microsoft Compliance Center to gain insights into your organization’s compliance posture as it relates to key standards and regulations like GDPR, ISO, and NIST. You can also perform risk assessments and follow guidance that’s provided in order to improve your privacy controls and compliance.
Microsoft Cloud Apps Security Insights, or MCAS, is available from the Compliance Center as well. You can use MCAS to do things like identify compliance risks across apps, monitor noncompliant employee behavior, and even identify shadow IT situations.
Once you’ve enabled the Microsoft Compliance Center for your tenants you can access it at this URL.
What You’ve Learned
Congratulations! You’ve reached the end of Compliance in Microsoft 365! Let’s review what you’ve learned.
In this chapter, we looked at a few key Microsoft 365 compliance tools. We started things off by covering the Service Trust Portal and Compliance Manager. You learned what they are, how to access them, and what features they offer. We then looked at Compliance Center, where you learned what information it provides and how to access it.
CHAPTER 8: Microsoft 365 Security Features
 Welcome to Microsoft 365 Security Features. In this chapter, we are going to review a few key Microsoft 365 security features.
Welcome to Microsoft 365 Security Features. In this chapter, we are going to review a few key Microsoft 365 security features.
We will start things off by covering identity and access in Microsoft 365. We'll look at secure authentication solutions, conditional access, and identity protection.
Next, we’ll cover key threat protection solutions that Microsoft 365 offers. We'll review Azure Active Directory Identity Protection, Advanced Threat Protection, Azure Security Center, and a few others.
After covering the key threat protection solutions in Microsoft 365, we'll take a look at the Microsoft Security Center and the Secure Score.
Identity and access in Microsoft 365
Identity and access management is probably the most important security pillar in Microsoft 365. By offering secure authentication, Microsoft 365 helps you protect against account breaches. Conditional access that is offered by Microsoft 365 offers granular access to corporate data. Identity protection features in Microsoft 365 can be used to ensure hackers do not steal the identity of your users.
Let’s start things off by taking a look at how Microsoft 365 provides secure authentication.
Secure Authentication
Protecting your organization against breaches means you need to protect your users. Ensuring that your users use complex passwords is one way to protect them. However, such complex passwords can be difficult to remember - and because complex passwords are so difficult to remember, users will often just use the same complex password for all of their sites and resources.
Relying solely on complex passwords can also be problematic because no matter how complex the passwords are, they are subject to replay attacks and they are often exposed due to phishing attacks. This obviously presents challenging security risks, especially since most breaches originate with compromised passwords.
To help reduce the risks associated with passwords, Microsoft 365 offers a few replacement options. These options include Multi-Factor Authentication, Windows Hello, and Microsoft Authenticator.
Multi-Factor Authentication, or MFA, allows you to specify multiple factors for authentication. It forces users to provide at least two authentication factors to identify themselves. These factors typically consist of something the user knows, such as a password or pin, something the user has, which would often be a smart card or digital certificate or even a phone, and it’s something the user is, which is usually some sort of biometrics.
Windows Hello is a Windows 10 feature that replaces passwords with two factor authentication on both PCs and mobile devices. This is a newer type of user credential that gets tied to a specific device and leverages either a pin or some form of biometric. Users can use Windows Hello to authenticate in Active Directory and in Azure Active Directory.
Microsoft Authenticator is an application that organizations can use to keep accounts secure. It works by offering two factor verification and phone sign in. Two factor verification is the standard verification method. The first factor is the user’s password. However, once a user signs into a device, app, or site, using his username and password, the user must use Microsoft Authenticator to either approve a notification or answer a verification code that is provided.
The phone sign-in option is another version of two factor verification that allows users to sign in without a password. Instead of using a username and password combination, users can login with a username and a mobile device with a fingerprint, face, or pin.
Conditional Access
Conditional access allows organizations to provide granular access to data and applications. It allows users to work from virtually any location and from just about any device. Conditional Access evaluates users, devices, apps, location, and risk before granting a specific user access to a corporate resource. This ensures that only those approved users can access company resources from only approved devices.
 Conditional Access evaluates access requests against several different criteria. It then compares this criterion to policies that you define. After comparing against these policies, Conditional Access will decide whether or not access is allowed.
Conditional Access evaluates access requests against several different criteria. It then compares this criterion to policies that you define. After comparing against these policies, Conditional Access will decide whether or not access is allowed.
I should mention that Conditional Access spans multiple Microsoft 365 services including Office 365, Windows 10, and InTune.
Identity Protection
Because most security breaches occur as a result of stolen user identities, identity protection is critical. Not only do you need to protect all of your user identities from being compromised, but you also need to ensure that you are proactively preventing compromised identities from being abused.
Microsoft 365 offers several ways for organizations to protect their identities. They include Azure Active Directory Identity Protection, Microsoft Cloud App Security, Azure Advanced Threat Protection, and Windows 10’s built-in identity protection capabilities.
Azure Active Directory Identity Protection helps organizations identify attempts to compromise user accounts. Whenever it identifies unusual behavior from an account, Azure Active Directory Identity Protection can block access and even require additional authentication options.
Microsoft Cloud App Security provides analytics for cloud apps and services. This helps organizations understand protections that are in place for their data across cloud apps.

Azure Advanced Threat Protection, or ATP, is a cloud-based security solution. Using ATP, organizations can identify, detect, and investigate many different threats, compromised identities, and other malicious activity that’s directed at the organization.
The built-in identity protection capabilities of Windows 10, including Windows Hello, can be used to further protect user identities.
So, as you can see by providing secure authentication, conditional access, and identity protection features, Microsoft 365 helps organizations manage the first security pillar which is identity and access management by helping them identify who is accessing resources and helping them control what can be accessed.
Threat Protection in Microsoft 365
Organizations that leverage Azure Active Directory get the benefits of the adaptive machine learning algorithms that it uses to detect suspicious incidents and identities that may be compromised. This data is used by Azure Active Directory Identity Protection to create reports and alerts that you can use to evaluate potential security issues and take action.
In addition to monitoring and reporting, Azure Active Directory Identity Protection allows you to configure risk-based policies that will automatically respond to suspicious incidents that are detected. These policies can be used with conditional access controls to automatically block access and to even automatically take remediation actions.
Azure Advanced Threat Protection
Azure Advanced Threat Protection, or ATP, is a cloud-based security solution. What Azure Advanced Threat Protection does is identify and detect advanced threats, compromised identities, and certain malicious insider actions. The security reports and analytics that ATP offers are useful for reducing your organizations attack surface.
Azure Security Center
Azure Security Center is another security tool. It offers advanced threat protection and unified security management across hybrid cloud workloads, which include those workloads on-prem, in the Azure cloud, and in other clouds. Azure Security Center will even allow you to automatically discover and onboard new Azure resources. Defined security policies are automatically applied to ensure such new resources are compliant with your security standards. You can use Azure Security Center to collect and analyze security data from many different sources, including firewalls and even partner solutions.

Microsoft Exchange Online Protection
The Microsoft Exchange Online Protection service, or EOP, is a cloud-based email filtering service provided to Microsoft exchange online customers. This anti-spam and antimalware solution provides email protection.
Microsoft InTune
Microsoft InTune is a mobile device management solution that is part of enterprise mobility and security, or EMS. It integrates with other EMS components as well. For example, its integration with Azure Active Directory helps provide identity and access control, while its integration with Azure information protection helps secure data. Using Microsoft InTune with office 365 can help protect your data while allowing users to work from virtually any device.
Office 365 Advanced Threat Protection
Office 365 Advanced Threat Protection is a security offering that is included in Microsoft 365 E5 subscriptions. It is used to identify threats before they make their way into a user’s mailbox by scanning email and URLs, identifying and blocking malicious files, and detecting impersonation attempts. The safe links feature of Office 365 Advanced Threat Protection scans emails in real time. Users are presented with a warning message if they click on a link that may be malicious. Attack Simulator, which comes with Advanced Threat Protection, can be used to simulate realistic attacks as well.
Office 365 Threat Intelligence
Office 365 Threat Intelligence consists of insights and other information - and is available in the Office 365 Security and Compliance Center. This tool can be used to understand different threats against your users and data because it monitors different signals and gathers data from several different sources, including email, compromised PCs, user activity, and other security incidents.
By leveraging these many different security tools, you can protect your users, identities, devices, user data, apps, and infrastructure.
Microsoft 365 Security Center and the Secure Score
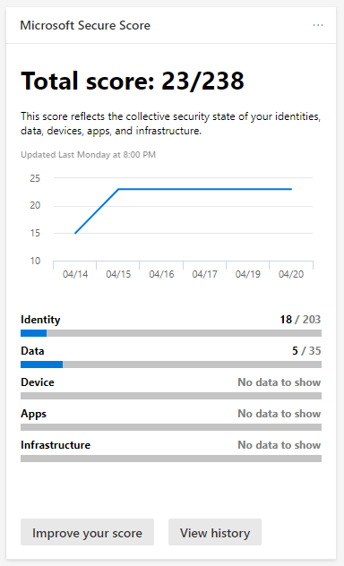 The Microsoft Security Center is used to track and manage security for identities, data, devices, apps, and even infrastructure. Security Center will generate alerts when suspicious activities are identified. The real-time reports that Microsoft Security Center offers allow organizations to keep track of issues within their organization. Because it provides many different insights and recommendations, the Microsoft Security Center can help organizations improve their security posture. You can even use the security Center to configure device and data policies.
The Microsoft Security Center is used to track and manage security for identities, data, devices, apps, and even infrastructure. Security Center will generate alerts when suspicious activities are identified. The real-time reports that Microsoft Security Center offers allow organizations to keep track of issues within their organization. Because it provides many different insights and recommendations, the Microsoft Security Center can help organizations improve their security posture. You can even use the security Center to configure device and data policies.
Within the Microsoft Security Center, you’ll find the Microsoft Secure Score. The Secure Score is a configurable security score assigned to your environment. This score provides an overall view of your security posture. You can use the centralized dashboard to not only monitor the security of your environment, but you can also use it to improve that security.
The Microsoft Secure Score offers detailed data visualization as well as integration with other Microsoft products. You can even use it to compare your score with other companies. By completing the improvement actions that are called out, you can improve your score and harden your environment.
The way that the Secure Score works is rather straightforward. It assigns points whenever you configure its recommended security features and when you perform certain security related tasks. It also assigns points for addressing certain improvement actions. The idea is to get your Secure Score as high as you can, while balancing the security and usability in your environment, because some recommendations won’t necessarily work in your environment, given how you do business.
Ultimately, what you want to do is use the Microsoft Secure Score recommendations to identify the most important settings to you and to make changes that you deem necessary.
What You’ve Learned
Congratulations! You’ve reached the end of Microsoft 365 Security Features. Let’s review what you’ve learned.
We started things off by covering identity and access in Microsoft 365, where we looked at secure authentication solutions, conditional access, and identity protection.
Next, we covered the key threat protection solutions that Microsoft 365 offers. We reviewed Azure Active Directory Identity Protection, Advanced Threat Protection, Azure Security Center, and a few others.
After covering the key threat protection solutions in Microsoft 365, we looked at the Microsoft Security Center and the Secure Score.
CHAPTER 6: Teamwork in Microsoft 365
 Welcome to Teamwork in Microsoft 365! In this chapter, we are going to cover teamwork in Microsoft 365 and analytics in Microsoft 365.
Welcome to Teamwork in Microsoft 365! In this chapter, we are going to cover teamwork in Microsoft 365 and analytics in Microsoft 365.
We will kick things off by looking at the different teamwork tools that are available in Microsoft 365 and how to choose the right teamwork tools for your needs. We'll look at tools like SharePoint Online, Outlook, Microsoft Teams, and more.
Next, we'll take a look at the different ways you can work together on files and content and how you can use teamwork tools to run meetings and projects.
We'll round things out by touching on the analytic tools that Microsoft 365 includes, where you'll learn about MyAnalytics and about Workplace Analytics.
Facilitating Teamwork in Microsoft 365
Microsoft 365 offers several tools and services that help teams of all sizes and shapes get their work done. The purpose of these tools is to streamline productivity while providing enterprise-level security, compliance, and manageability.
Using Microsoft Outlook, users can share calendars, files, tasks, while keeping in touch with coworkers.
SharePoint and OneDrive for business can be used to store content. This content can be accessed from virtually any device and even shared with other users, both inside and outside the organization. Users can collaborate on this content using applications such as Word, Excel, and PowerPoint.
 Microsoft Teams allows users to communicate via chat, phone calls, and meetings. It can also be used to share content. Microsoft Teams also offers guest access that allows users to invite both internal and external users to work on projects.
Microsoft Teams allows users to communicate via chat, phone calls, and meetings. It can also be used to share content. Microsoft Teams also offers guest access that allows users to invite both internal and external users to work on projects.
Yammer is another communications tool offered with Microsoft 365. It’s a community conversation tool that encourages dialogue and idea generation across the organization. With yammer, you can create different communities of interest, as well as forms that bring people together. Yammer also allows you to grant external access when you need to.
Other teamwork tools available in Microsoft 365 include Microsoft Graph and Office 365 Groups. Using Microsoft graph provides a seamless connection between people and relevant content, while Office 365 groups enables a single team identity across applications and services, along with a centralized policy management system that enhances security and compliance for your organization.
Choosing the Right Tools
Choosing the right tools for your organization is important to ensuring your team members have what they need to complete their jobs. Those team members can be categorized as inner loop or outer loop.
Inner loop users are those who you actively work with on a day-to-day basis. To facilitate communications with inner loop users, you should probably use Microsoft Teams.
Outer loop users are users that you don’t necessarily work with on a regular basis but who have a vested interest in whatever project it is that you are working on. Project stakeholders would be a good example of outer loop users when it comes to a specific project because, while you won’t necessarily work with them on a regular basis, they do want to hear what’s going on with the project they are involved in. In these cases, you could use Yammer to share information and ideas. An alternative for those who prefer email, would be Outlook.
SharePoint should be your tool of choice when you need to manage team content and files because it essentially brings together the content from Microsoft Teams, Yammer, and Outlook. You can also use SharePoint to keep track of your project information.
Working Together
Because users will often need to work together in real time, on a specific document, Microsoft 365 offers co-authoring capabilities with all core office applications.
For example, your users can co-author a Word document when it is stored in OneDrive for Business or even in SharePoint. Presence information that Microsoft Teams offers adds to the co-authoring experience, while providing a chat-based workspace for those users who are actively working on the document that they are co-authoring.
The shared storage, versioning controls, and permission settings that OneDrive for Business and SharePoint offer allow multiple users to edit the same document seamlessly.
Through Microsoft Teams, all users on a given team, including external users, have a single point of access to all the tools they need to move their projects forward. Because Teams is integrated with applications like Word, Excel, PowerPoint, Power BI, and Stream, team members are able to collaborate without leaving the shared Teams workspace.
When team members work on files in Teams, those files are automatically stored in SharePoint. Team members can hold chats and collaborate on shared deliverables.
I should note that you can customize Microsoft Teams to fit your environment. For example, you can enable, disable, and configure apps for Teams - this includes tabs, connectors, and lots of other features provided by Teams. You can specify whether external applications are enabled, and you can control which users can sideload apps. Organization-wide user settings like guest access and external access can be configured as well. These settings allow users to work with people outside the organization. There are many other settings that can be configured as well, including filesharing, cloud file storage, email integration, and more.
Meetings and Projects
It should come as no surprise that most workers spend as much as one-third of their time in meetings. Nobody likes them, but they are a necessity. Microsoft 365 makes meetings less painful and more productive by allowing users to not only easily schedule calls and online meetings, but to also quickly start them through a call or instant message.
Microsoft 365 also allows you to create shared workspaces to host all of your Teams meetings, files, apps, and even team conversations. Microsoft 365 automates processes and workflows and allows you to save time by leveraging self-service tools to manage and schedule tasks.
Outlook’s calendar and file integration make it easier for users to leverage meeting tools seamlessly. Team members can even access shared calendars and link to shared files in both SharePoint and in OneNote. Microsoft Teams organizes conversations, files, meetings, and tools into a single hub that also offers audio and video capabilities. Video and screen sharing capabilities of Microsoft Teams, along with features like auto translation, transcription, and recording, allow users to get more out of the experience. Notes and action items can even be automatically transcribed and distributed to meeting attendees at the end of the meeting.
Analytics in the Workplace
Microsoft 365 offers two analytic tools. These analytic tools include MyAnalytics and Workplace Analytics. Both of these tools gather data and use artificial intelligence to provide insights into the working habits of your users and your organization.
MyAnalytics can be used to see how you are spending your time at work. It then suggests different ways that you can work smarter instead of harder. To allow this magic to happen, MyAnalytics, which is included in Microsoft 365 E5 subscriptions, looks at email data, meetings, team chats, calls, and how you use Office 365. There are no agents to install, nor is there any tracking software to deal with.
I should point out for the security conscious that MyAnalytics does not use any data from any from your other activities such as applications or websites that you view.
To learn more about MyAnalytics, visit this URL.
Workplace Analytics focuses on the organization as a whole. This is different from MyAnalytics, which provides insights at the individual level. Using Workplace Analytics allows you to identify collaboration processes that impact your organization’s productivity and workforce effectiveness. Workplace Analytics helps organizations understand how they spend their time and how their groups work together. This allows those organizations to define best practices and to become more efficient.
To read more about Workplace Analytics, visit this URL.
What You’ve Learned
Congratulations! You've reached the end of Teamwork in Microsoft 365! Let's review what you've learned.
Throughout this chapter, we covered teamwork features in Microsoft 365 and analytics in Microsoft 365.
We kicked things off by looking at the different teamwork tools that are available in Microsoft 365 and how to choose the right teamwork tools for your needs. We also looked at tools like SharePoint Online, Outlook, Microsoft Teams, and more.
Next, we looked at the different ways you can work together on files and content and how you can use teamwork tools to run meetings and projects.
We rounded things out by touching on the analytic tools that Microsoft 365 includes, where you learned about MyAnalytics and about Workplace Analytics.
At this point, you should be able to intelligently evaluate the many different teamwork tools in Microsoft 365.
CHAPTER 5: Unified Endpoint Management
 Welcome to Unified Endpoint Management. In this chapter, we are going to cover unified endpoint management topics.
Welcome to Unified Endpoint Management. In this chapter, we are going to cover unified endpoint management topics.
We will start things off with device management in today’s workplace. You’ll learn about key unified endpoint management concepts and how IT departments can support different devices in the modern workplace.
Next, we’ll cover the many different components of the Enterprise Mobility and Security suite. You’ll learn about Azure AD, SCCM, Azure Information Protection, and much, much more. You’ll learn what each component is and what role each component plays.
Rounding things out, we’ll get into cloud-connected device management, where you’ll learn about the different ways that you can manage cloud-connected devices.
We have quite a bit to get to. So, let’s get started.
Device Management in the Modern Workplace
Unified endpoint management refers to a platform for managing devices and applications. Using Microsoft InTune and System Center Configuration Manager, both of which are parts of Enterprise Mobility and Security within a Microsoft 365 subscription, can help simplify management. Using these products creates an environment that allows end users to use whatever devices and applications they choose, while still offering protection for the organizations data.
The modern workplace presents unique challenges for IT departments because they need to support many different devices that are configured in many different ways. Some users may have Android devices, while others may use iOS smartphones. Yet others may use Windows 10 machines, while others use Macs. In addition to supporting the devices themselves, IT departments need to ensure that these devices all meet the security standards and health standards that are established by the organization. Such devices also need to be configured to support whatever applications and features the organization uses.

Each of these different devices clearly presents different management challenges. For example, users will often use mobile devices and laptops that connect to outside networks through public Wi-Fi access points. Because hackers will often use public access points to capture network traffic and insert malware into a user’s browsing sessions, the fact that mobile devices often connect to unsecured networks like these can impact every user in the organization.
While devices that connect to unsecured networks can be a problem, so can mobile devices that only intermittently connect to the corporate network. This is because tools like Group Policy, which are used to manage devices, usually assume that these devices are always connected to the corporate network. Because they are not, these mobile devices can be difficult to manage with traditional tools.
Users will often connect to the corporate network and access files from central file shares and from SharePoint sites. While these centralized storage locations are often backed up, mobile devices, which include laptops, typically are not. Because these devices aren’t backed up, any data that is created directly on them is not backed up either. If one of these devices is stolen or suffers a serious hardware failure, this locally created data is lost.
 Speaking of lost or stolen devices… Quite often, the cost of replacing a stolen device can far exceed the original cost of the device itself. This is because the organization needs to not only replace the device, but it also needs to configure the device and determine what data was lost or stolen. This all requires time - and time is money.
Speaking of lost or stolen devices… Quite often, the cost of replacing a stolen device can far exceed the original cost of the device itself. This is because the organization needs to not only replace the device, but it also needs to configure the device and determine what data was lost or stolen. This all requires time - and time is money.
Another struggle that IT departments deal with are devices that have been compromised and then connected to the corporate network. This is a problem because a device that’s been infected with malware cannot only steal data, but also spread the malware to other devices in the organization. Because of this, mobile devices must be treated as potential threats, and precautions must be taken to prevent attacks and to prevent leaks.
Personal devices also pose significant challenges to most organizations because those organizations need to decide if they wish to allow users to access corporate apps and data from their personal devices. This requires organizations to implement mobile device support policies. Organizations need to decide whether they will allow user owned devices to access corporate applications and data or if they will only allow this access only if the owner of the device allows the organization to manage the device. Organizations also need to decide what actions can be taken to protect any corporate data that is stored on the device. In the event the device is lost or if the user leaves the company.
The proliferation of BYOD in today’s modern workplace has made work easier for end users, but as you can see, it also presents significant challenges to IT departments.
Enterprise Mobility + Security Components
Enterprise Mobility + Security is a tool that you can use to manage all devices within your organization. It’s intended to help organizations protect and secure their environments. The EMS suite of products comes included with Microsoft 365 E3 and E5 plans.
The table below provides a summary of what is included.
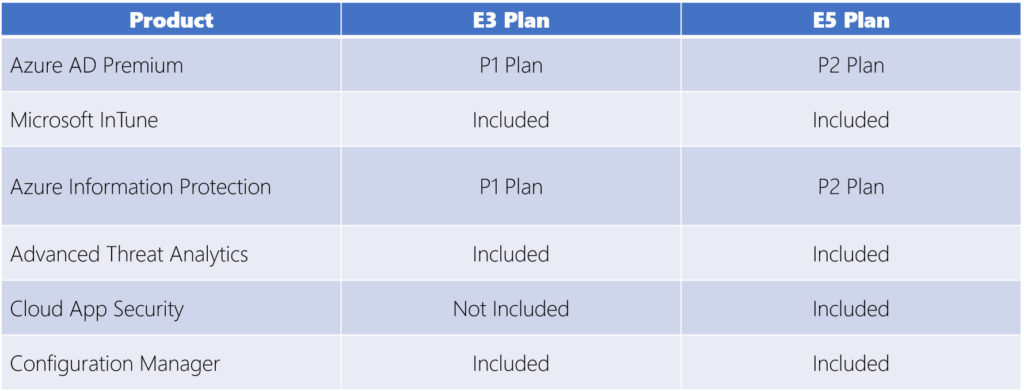
Azure AD Premium is a central identity store. All applications in EMS and in Microsoft 365 use this identity store. There are three different levels of Azure AD premium. They include Basic, P1, and P2. The Basic level includes basic features that can be used to facilitate endpoint management. However, the P1 and P2 plans come with additional features, including Self-Service Password Reset, Write-Back from Azure AD to On-Prem Active Directory, and Microsoft Azure MFA for Cloud and On-Prem Apps. Other features that come with the P1 and P2 plans include Conditional Access Based on Group, Location, and Device, and in the case of P2, Conditional Access Based on Sign-In or User Risk.
Another component to EMS, is InTune. This cloud-based enterprise mobility management service protects corporate data while facilitating end-user productivity. Identity and access control are achieved through its integration with Azure AD, while data protection is achieved through its integration with Azure Information Protection. You can also use InTune to enforce security policies, deploy applications, and even remotely wipe devices when they are lost or stolen.
System Center Configuration Manager, or SCCM, is an on-prem product that organizations can use to manage Windows PCs, Mac OS PCs, and servers. This product allows organizations to customize application management, OS deployments, and even device compliance.
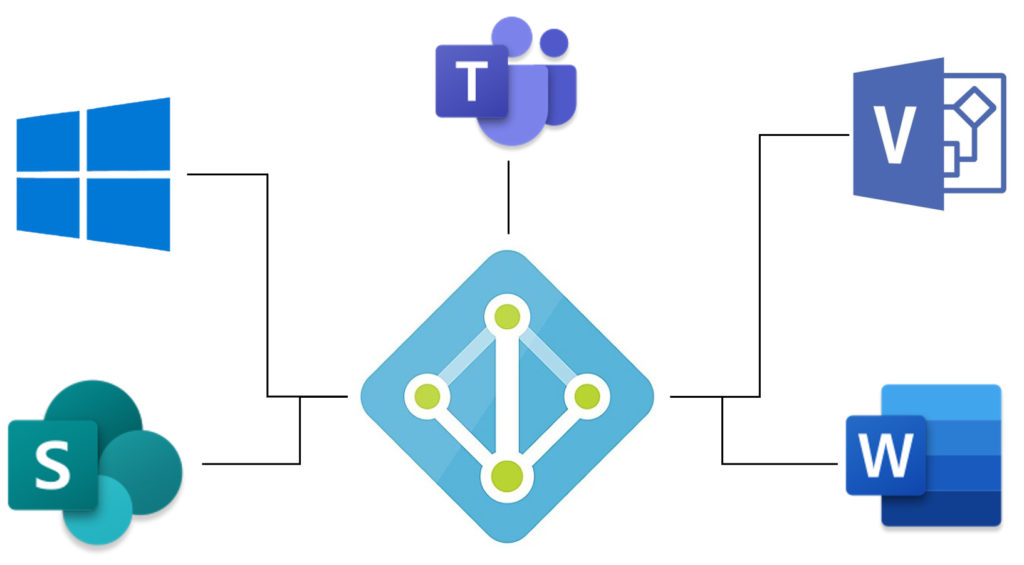
Azure Information Protection, or AIP, is a component of EMS that organizations can use to encrypt documents and to enforce policies on how those documents can be used.
Microsoft Advanced Threat Analytics is another component of EMS. With Advanced Threat Analytics, organizations can detect suspicious activities and malicious attacks. This allows them to adapt to the ever-changing landscape of cybersecurity threats. Microsoft Advanced Threat Analytics also helps organizations reduce false positives.
Cloud App Security is an add-on that can be combined with your organizations Microsoft 365 subscription. It provides visibility into cloud apps and services, while also providing analytics that you can use to identify and mitigate security threats.
Cloud App Security takes data that’s been collected from your organization’s firewalls and proxy servers and uses it to track cloud application usage. Using Cloud App Security, you can identify unauthorized applications that are in use and that might be a threat to your organization. It also allows organizations to identify unusual usage patterns.
Microsoft Identity Manager essentially combines Microsoft’s identity and access management solutions together. It takes different on-prem authentication stores, including AD, Oracle, LDAP, and others, and bridges them with Azure AD to provide a consistent identity experience for on-prem applications as well as SaaS solutions.
Azure Advanced Threat Protection, or ATP, is a cloud-based solution that allows organizations to not only identify and detect threats and malicious activities but to also investigate them as well. You can use Azure Advanced Threat Protection to identify suspicious user and device activity and to analyze threat intelligence from the cloud, and on-prem. Azure Advanced Threat Protection helps protect user identities and credentials that are stored in Active Directory and allows you to view attack information on a simple timeline. This allows for faster triage.
As you can see, Enterprise Mobility and Security offers quite a few tools that you can use to manage security and devices within your organization.
Cloud-Connected Device Management
If your organization already uses Configuration Manager on-prem to manage devices, it can be connected with the cloud-based InTune management system through the co-management function of Configuration Manager. When you connect the two using the co-management function, you can manage your Windows 10 devices with both Configuration Manager and Microsoft InTune at the same time. What this does is add InTune functionality to your device management solution.
Connecting Configuration Manager with the cloud-based InTune management system provides several benefits over using Configuration Manager alone. For example, with this cloud connected system, you can use conditional access to make sure that only trusted users can access corporate resources from trusted devices, using trusted apps.
You can also manage all registered devices every time they connect, regardless of where they are. These remote actions allow you to wipe such devices when they are lost or stolen. You can also rename and restart devices remotely, and even perform factory resets on Windows devices.
While Configuration Manager can monitor the health of your devices while they are connected to the network, Microsoft InTune can communicate with co-managed devices, and monitor their health, even when they are not connected to the network - and it can report on the health of those clients.
To ensure that new devices that are added to your network get configured the same way as existing devices, you can use co-management and Windows 10 Autopilot together. When you use Windows 10 Autopilot and co-management together, you can take advantage of the Windows 10 provisioning model, which helps eliminate the need to deal with creating and updating custom operating system images.
Leveraging Azure Active Directory lets you link users, devices, and applications from both cloud and on-prem environments. When you register your organizations devices to Azure AD, you can improve security while increasing productivity of your end users. Registering devices in Azure AD provides the ability to co-manage them and to leverage device-based conditional access. It also allows you to offer single sign-on to cloud resources, automatic device licensing, self-service functionality, Windows Hello for Business, and enterprise state roaming.
So, with that said, if you have an existing on-prem Configuration Manager infrastructure, connecting it with a cloud-based InTune management system through the co-management function allows you to reap significant benefits.
What You’ve Learned
Congratulations! You've reached the end of Unified Endpoint Management. Let's review what you've learned.
Throughout this chapter, you learned about several unified endpoint management topics.
We started things off with device management in the modern workplace. You learned about key unified endpoint management concepts and how IT departments can support different devices in the modern workplace.
Next, we covered the many different components of the Enterprise Mobility and Security suite. You learned about Azure AD, SCCM, Azure Information Protection, and much, much more. You also learned what each component is and what role each component plays.
Rounding things out, looked at cloud-connected device management, where you learned about the different ways that you can manage cloud-connected devices.
At this point, you should have a pretty good understanding of unified endpoint management options in Microsoft 365.
CHAPTER 4: DEPLOYING WINDOWS 10 AND OFFICE 365
 Welcome to Deploying Windows 10 and Office 365 ProPlus. In this chapter, we are going to cover the different ways that you can deploy Windows 10 and Office 365 ProPlus in your environment. We will start things off by covering the steps you need to take to plan for Windows 10 and Office 365 ProPlus deployments. We’ll cover hardware assessment and application compatibility assessment, along with network assessment and optimization.
Welcome to Deploying Windows 10 and Office 365 ProPlus. In this chapter, we are going to cover the different ways that you can deploy Windows 10 and Office 365 ProPlus in your environment. We will start things off by covering the steps you need to take to plan for Windows 10 and Office 365 ProPlus deployments. We’ll cover hardware assessment and application compatibility assessment, along with network assessment and optimization.
Next, we’ll cover the different deployment options for Windows 10. We’ll look at things like Windows autopilot, in-place upgrades, and dynamic provisioning. We will also look at subscription activation as a means for switching from one edition of Windows 10 to another.
After covering the deployment options for Windows 10, will take a look at the different deployment options for Office 365 ProPlus. We will take a look at Configuration Manager, the office deployment tool, and manual installation from the Office 365 portal.
Once we finish working through the different Office 365 ProPlus deployment options, we’ll cover servicing channels and deployment rings.
Coming down the home stretch, we will cover updates for Office 365 ProPlus. We’ll take a look at the different update channels for Office 365 ProPlus including the Monthly Channel, the semiannual targeted channel, and the Semi-Annual Channel. In this lecture, you’ll learn how to choose the appropriate update channel for your organization and how updates are installed for Office 365 ProPlus.
Rounding things out, we’ll dive into licensing and activation in Office 365 ProPlus, where you’ll learn about licensing Office 365 ProPlus, reduced functionality mode, and how to activate Office 365 ProPlus. You’ll also learn how to manage activated installations.
Planning Deployments
When planning an enterprise deployment of Windows 10 and Office 365 ProPlus, you need to ensure that you properly assess your environments and your network. You also need to make sure that any existing hardware and applications in your environment will work with your new software.
Assessing Compatibility
Although virtually all applications that have been written in the last decade will run on Windows 10 - and virtually all add-ins and VBA macros that are based on previous versions of Office will work in the latest versions of Office - your organization should ensure that existing applications and hardware will support Windows 10 and Office 365 ProPlus before rolling them out.
To help with this process, Microsoft offers several different tools.

The Windows Analytics Upgrade Readiness Tool is provided to assess desktop, device, and application readiness. This tool provides information about application and driver compatibility, and it provides a detailed assessment of any identified issues that could prevent an upgrade. It also provides links to suggested fixes for any issues it identifies.
The Readiness Toolkit for Office Add-Ins and VBA is designed to help organizations identify compatibility issues with existing Microsoft VBA macros and add-ins. This tool scans for VBA macros in Word, Excel, PowerPoint, Access, Outlook, Project, Visio, and Publisher files.
Desktop App Assure is a new service that you can use to address issues with Windows 10 and Office 365 ProPlus application compatibility. This service comes with the Fast-Track Center Benefit for Windows 10. To get access to the Fast-Track Center Benefit for Windows 10, you must have an eligible subscription. An eligible subscription is one that includes at least 150 licenses for an eligible service or plan for your Office 365 tenant.
 Before deploying Windows 10 and Office 365 ProPlus in production, Microsoft recommends that you first deploy them to a pilot group of users on a pilot group of devices across the organization. By testing your deployment with a pilot group first, you can mitigate any issues that crop up before you deploy into production.
Before deploying Windows 10 and Office 365 ProPlus in production, Microsoft recommends that you first deploy them to a pilot group of users on a pilot group of devices across the organization. By testing your deployment with a pilot group first, you can mitigate any issues that crop up before you deploy into production.
Network Assessment and Optimization
Before deploying and managing updates for Windows 10 and Office 365 ProPlus, you need to ensure you have the necessary bandwidth to do so. The Office 365 ProPlus installation files are at least 1.6 GB in size – and this is just for the core files. Each language that you deploy will add another 250 MB.
To help deal with network bandwidth limitations, there are several built-in methods for automatically limiting bandwidth. Express Update Delivery and Binary Delta Compression both help reduce the size of your update downloads. These methods ensure that you only download the changes that have occurred between the current update and the previous update. This typically vastly minimizes the impact to your network.
There also peer-to-peer options available. These options essentially shift Windows 10 and Office 365 ProPlus traffic away from the center of your network. What this does is reduce the need for throttling. Using a peer-to-peer option allows computers to find necessary update files on other machines in the local network, instead of downloading those files from a central distribution share on the network or from the internet.
There are currently three peer-to-peer options available. These options include Branch Cache, Peer Cache, and Delivery Optimization.
 Branch Cache allows you to download source files in a distributed environment without crushing your network. What Branch Cache does is retrieve the content from the main office or from hosted cloud content servers. It then caches that content at your branch office locations. Users from these locations can then access that content locally instead of accessing it over the WAN.
Branch Cache allows you to download source files in a distributed environment without crushing your network. What Branch Cache does is retrieve the content from the main office or from hosted cloud content servers. It then caches that content at your branch office locations. Users from these locations can then access that content locally instead of accessing it over the WAN.
Peer Cache comes with Configuration Manager. It allows clients to share source files directly from other clients. Organizations will often use Peer Cache to manage the deployment of source files to users in remote locations. You can use Branch Cache and Peer Cache together in the same environment.
With Delivery Optimization, your clients can download source files from alternate sources, including other peers on the local network. This is in addition to Windows Update Servers. Delivery Optimization can be used with Windows Update, Windows Server Update Services (WSUS), Windows Update for Business, and Configuration Manager.
By assessing hardware and application compatibility, and assessing and optimizing your network, you can ensure a smooth deployment of Windows 10 and Office 365 ProPlus.
Windows 10 Deployment Options
There are actually quite a few ways to deploy Windows 10 in an organization. You can use existing tools such as InTune, Azure AD, and Configuration Manager OR you can you one of several new deployment tools and methods that are now available. These new tools and methods include Windows Autopilot, In-Place Upgrades, Dynamic Provisioning, and Subscription Activation.
With Windows Autopilot, you can customize the out of box experience (OOBE) so that you can deploy applications and settings that are preconfigured specifically for your organization. This allows you to include just the applications that your users need. Windows Autopilot is probably the easiest way to deploy new PCs that run Windows 10. It can also be used in conjunction with Configuration Manager to upgrade Windows 7 and Windows 8.1 machines to Windows 10.
Leveraging In-Place Upgrades allow you to upgrade to Windows 10 without reinstalling the OS. This method allows you to migrate applications, user data, and settings from one version of Windows to another. You can also use an in-place upgrade to update a Windows 10 machine from one release to the next.
Dynamic Provisioning allows you to create a package that you can use to quickly configure multiple devices, even those that have no network connectivity. Using Windows Configuration Designer, you can create provisioning packages and install them over the network, or even from a USB drive. They can also be installed in NFC tags or barcodes.
Using Subscription Activation, you can use subscriptions to switch from one edition of Windows 10 to another. An example of this would be a scenario where you need to switch a user from Windows 10 Pro to Windows 10 Enterprise. In this scenario, if a licensed user signs into the Windows 10 device, assuming the user has a Windows 10 E3 or E5 license, the operating system automatically changes from Windows 10 Pro to Windows 10 Enterprise. This unlocks the Windows 10 Enterprise features. I should mention that if the associated E3 or E5 license expires, the Windows 10 device simply reverts back to the Windows 10 Pro addition. You are, however, offered a grace period of up to 90 days before it reverts back.
So, as you can see there are several ways to deploy Windows 10.
Deployment Options for Office 365 ProPlus
There are several ways to deploy Office 365 ProPlus. Let’s take a look at the options that are available.
You can use Configuration Manager, the Office Deployment Tool, and Microsoft InTune to perform Office 365 ProPlus deployments. You can, of course, also install directly from the Office 365 portal.
Configuration Manager is a good choice for enterprises that already leverage a solution to deploy and manage their existing software. The Office Deployment Tool is a good choice for organizations who need to manage their Office 365 ProPlus deployment, but do not have Configuration Manager deployed. Organizations that wish to deploy and manage Office 365 ProPlus directly from the cloud should consider Microsoft InTune. However, the easiest approach to deploying Office 365 ProPlus is to just allow your users to install it directly from the Office 365 Portal. The caveat to this solution, though, is that it provides far less control over the deployment process.
When you deploy Office 365 ProPlus using the Office Deployment Tool or through Configuration Manager, you’ll typically create configuration files using the Office Customization Tool. These configuration files are then used to define the configuration of Office. This process provides you with more control over your installations. There are also similar options available when you use InTune to deploy Office 365 ProPlus.

I should mention here, that depending on how you decide to deploy Office 365 ProPlus, you can choose to deploy directly from the cloud or you can download Office to local storage on your network, where you can then deploy from. Microsoft, however, recommends that you deploy Office directly from the cloud because it minimizes administrative overhead. When deployed in this fashion, Office 365 ProPlus is installed on your client devices right from the Office Content Delivery Network. If you find that your internet bandwidth can’t support installations directly from the cloud, you can use Configuration Manager to manage your deployments and updates that can be pulled from a local network location.
The deployment option you choose will be largely dependent on your network infrastructure, your user base, and your corporate policies.
Windows-as-a-Service
Under the Windows-as-a-Service model, Microsoft has simplified the OS build and deployment process. Instead of providing major OS revisions every few years, with service packs released between those revisions, Windows updates are now treated more like ongoing maintenance tasks. This means that Windows will now receive updates and revisions on a more frequent basis. These updates and revisions are also applied with less disruption.
These new updates fall into two different buckets. These buckets include Feature Updates and Quality Updates. Feature Updates are updates that add new functionality. They are released twice a year and can be deployed using existing management tools. Feature Updates are typically smaller because they are more frequent. Because they are smaller, the impact to organizations when deploying them is reduced.
Quality Updates are security updates and fixes. These updates are typically issued once a month. More specifically, the second Tuesday of each month, otherwise known as Patch Tuesday. When a cumulative update is released on Patch Tuesday, it includes all previous updates. This makes it easier to ensure that devices are fully up to date.
You can use deployment rings and servicing channels to control how updates are applied - and when.
Servicing Channels
There are three servicing channels offered by Windows-as-a-Service. Each channel receives new feature updates on a different schedule. These channels include the Semi-Annual Channel, the Long-Term Servicing Channel, and Windows Insider. The purpose of these servicing channels is to provide organizations with a way to control the frequency at which they deploy Windows 10 features.
Deployment Rings
Deployment rings are similar to machine groups that you may have used previously to manage updates for earlier versions of Windows in WSUS. There used to gradually deploy Windows 10. You can use deployment rings to group devices together and to ensure those devices receive their updates through the same servicing channels.
You can use the same management tools to deploy servicing channel updates that you used in earlier versions of Windows. For example, you can use the Windows Insider program to allow users to familiarize themselves with Windows features before they are released to the larger population of users within the organization. This allows organizations to get a look at early builds and to test them before they are released to the general public.
You can use the Semi-Annual Channel to receive updates as soon as Microsoft publishes them. Feature updates go out to the Semi-Annual Channel Once in the spring and once in the fall.
You can also use the Long-Term Servicing Channel to deploy updates to your organization. The Long-Term Servicing Channel is for computers and other devices that essentially perform a single task or several specialized tasks. For these types of computers and devices, the Long-Term Servicing Channel prevents them from receiving feature updates. However, quality updates are not affected. I should point out that the Long-Term Servicing Channel is only available in the Windows 10 Enterprise LTSC edition. Feature updates are released to LTSC about once every three years.
A typical deployment ring strategy might consist of four rings. For example, the first ring may be a preview ring that leverages the Windows Insider Program. This ring would be reserved for a small group of devices that you wish to use for testing. The next ring would be the targeted ring, which leverages the Targeted Semi-Annual Channel. You would use this ring to evaluate important updates before you deploy them to other devices in your environment. The next ring would be the production ring. This ring would leverage the Semi-Annual Channel and would be used to deploy updates to production machines. A fourth ring might be a critical ring. This critical ring would leverage the Semi-Annual Channel as well, but it would be reserved for machines that are critical, and which are only updated after thorough testing throughout the rest of your organization.
Ring strategies like the one in this example allow organizations to control how updates are deployed to all of their devices.
Windows-as-a-Service, when leveraged properly, is essentially an ongoing process that you use to handle Windows updates in an organization. The servicing models that are available for managing Windows-as-a-Service updates include Windows Update (or standalone), Windows Update for Business, WSUS, and System Center Configuration Manager (SCCM).
Windows Update offers limited control over feature updates. Devices are typically manually configured to use the Semi-Annual Channel. An organization that uses Windows Update can specify when updates get installed and to what devices. I should also mention that the updates do not even have to come from an on-prem server.
Windows Update for Business provides control over update deferments while also allowing for centralized management through group policy. You can use Windows Update for Business to defer updates for up to a year. Devices that are updated using Windows Update for Business need to be updated periodically and monitored using one system.
Windows Server Update Services, or WSUS, allows for significant control over Windows updates. This tool, which is native to the Windows Server OS, allows organizations to not only defer updates, but to also add an approval layer for updates that allows organizations to specify groups of computers that should receive updates.
System Center Configuration Manager offers the most control and is the most cost-effective option to service Windows-as-a-Service. Updates can be deferred and approved by IT staff, and there are also multiple options for targeting and bandwidth management. System Center Configuration Manager allows for consistent scheduling of updates across all devices within the enterprise. I should point out, however, that application deployments and operating system updates must originate from an on-prem server when using system Center Configuration Manager.
So which servicing option, should you choose? Well, the servicing option that you choose will be largely governed by the resources you have available to you, your IT staff, and the knowledge of that IT staff. If you already use. System Center Configuration Manager to manage your Windows updates, it probably makes sense to continue using it. However, if you are already using a solution like WSUS, it probably makes sense to continue using WSUS. Your environment and your staff will ultimately determine which solution is right for you.
Office 365 ProPlus Updates
There are several types of updates that are available for Office 365 ProPlus. Let’s take a look at these types of updates and figured out how to choose the appropriate update channel for your organization.
Because Microsoft provides new features for Office 365 applications pretty regularly, it’s important that you keep it updated. Microsoft offers multiple update channels that you can use to keep Office 365 ProPlus updated. These channels are used to control how often Office 365 ProPlus receives feature updates.
The three primary update channels that are available for Office 365 ProPlus include the Monthly Channel, the Targeted Semi-Annual Channel, and the Semi-Annual Channel. The Monthly Channel, as you would expect, receives feature updates roughly every month. The Targeted Semi-Annual Channel receives feature updates in March and in September. Organizations will often use this channel for its pilot users and for application compatibility testing. The Semi-Annual Channel receives feature updates twice a year, once in January and again in July.
The feature updates that are released in the Semi-Annual Channel will generally have already been released through the Monthly Channel in prior months. I should note that the Semi-Annual Channel is the default update channel for Office 365 ProPlus.
Microsoft also provides additional updates for each channel as needed. These include Security Updates and Quality Updates. While Security Updates are often released on patch Tuesday, which is the second Tuesday of every month, they can be released at other times when needed. Quality Updates are non-security updates which are also released on patch Tuesday.
Choosing the Right Update Channel
Organizations obviously have different needs - and these needs will determine which update channels are needed. For example, an organization might leverage the Semi-Annual Channel if it uses business applications, add-ins, and macros that must be tested to ensure they work with an updated version of Office 365 ProPlus.
However, an organization that wants its users to have access to the latest Office 365 ProPlus features as soon as they become available might want to leverage the Monthly Channel, assuming there is no need for any kind of application compatibility testing.
It’s important to note that an organization can leverage different update channels for different users. Not all users need to be on the same channel.
Installing Updates for Office 365 ProPlus
When an Office 365 ProPlus update occurs, all updates for the specific channel are installed at the same time. For example, you won’t get a separate download for Security Updates, a separate download for Quality Updates, etc. They are all installed at the same time. I should also mention that updates are cumulative. This means that the latest update will include all previously released feature, security, and quality updates for the specific channel.
Office 365 ProPlus goes out and checks for updates on a regular basis. These updates are then downloaded and installed automatically. Although users can continue using their office applications while uploads are being downloaded, once the actual update installation begins, those users will be prompted to save their work and to close their apps to allow the installation of the downloaded updates.
Office 365 Licensing and Activation
Before you can deploy Office 365 ProPlus to your users, you first need to assign licenses to them. Once you’ve assigned licenses to your users, they can begin installing the software. Once licensed, each user can install Office 365 ProPlus on up to five different computers or devices. Because each installation is activated and kept activated automatically, you don’t even have to keep track of product keys. You also don’t have to worry about dealing with KMS or MAK services. What you do have to do, however, is ensure that your users connect to the internet at least once every 30 days so their licenses can be kept activated by the Office licensing service.

Licensing Office 365
Assigning an Office 365 ProPlus license to a user is as simple as checking a box on the licensing page for the users account. Once you’ve assigned licenses to your users, they can install office right from the Office 365 portal. You can also deploy Office to your end users from a shared location on your local network. Users cannot install Office from the Office 365 portal until they have been assigned a license.
Reduced Functionality Mode
If you remove a user’s Office 365 ProPlus license, any existing installations of Office 365 ProPlus for that user will go into what is called Reduced Functionality Mode. Deactivating a user’s Office 365 ProPlus license for a specific device will also cause Office 365 ProPlus to go into Reduced Functionality Mode, but only on that device.
An Office 365 ProPlus installation that has gone into Reduced Functionality Mode will remain installed on the computer; however, the user will only be able to view and print documents. They will not be able to edit documents nor create new documents.
I should also point out that every time the unlicensed user runs Office 365 ProPlus, that user will be prompted to sign in and activate the software.
Activating Office 365 ProPlus
When Office 365 ProPlus is installed, it communicates back to the Office Licensing Service and the Activation and Validation Service. It does this so it can obtain and activate a product key. Whenever a user logs into his computer, the computer will connect to the Activation and Validation service. This is done in order to verify the license status of the software and to extend the product key.
Office will remain fully functional as long as the computer connects to the internet at least once every 30 days. Office will enter Reduced Functionality Mode if a computer goes off-line for more than 30 days. Once the computer connects back to the internet, the Activation and Validation Service will automatically reactivate the installation and it will become fully functional again.
Managing Activated Installations
As I mentioned previously, an Office 365 ProPlus license allows a user to install Office on up to five different computers. However, if that user tries to install Office 365 Pro on sixth computer, the user will first need to deactivate one of the existing five installations. This causes the installation that is deactivated to go into Reduced Functionality Mode.
What You’ve Learned
Congratulations! You’ve reached the end of Deploying Windows 10 and Office 365 ProPlus. Let’s review what you’ve learned.
Throughout this chapter, we covered the different ways that you can deploy Windows 10 and Office 365 ProPlus in your environment. We started things off by covering the steps you need to take to plan for Windows 10 and Office 365 ProPlus deployments. We covered hardware assessment and application compatibility assessment, along with network assessment and optimization.
Next, we covered the different deployment options for Windows 10. We looked at things like Windows Autopilot, In-Place Upgrades, and Dynamic Provisioning. We also looked at Subscription Activation as a means for switching from one edition of Windows 10 to another.
After covering the deployment options for Windows 10, we reviewed the different deployment options for Office 365 ProPlus. We looked at Configuration Manager, the Office Deployment Tool, and Manual Installation from the Office 365 portal.
Once we finished working through the different Office 365 ProPlus deployment options, we dove into the Windows-as-a-Service model, where we covered servicing channels and deployment rings.
Coming down the home stretch, you learned about updates for Office 365 ProPlus. You learned about the different update channels for Office 365 ProPlus including the Monthly Channel, the Semi-Annual Targeted Channel, and the Semi-Annual Channel. You also learned how to choose the appropriate update channel for your organization and how updates are installed for Office 365 ProPlus.
Rounding things out we dove into licensing and activation in Office 365 ProPlus, where you learned about licensing Office 365 ProPlus, Reduced Functionality Mode, and how to activate Office 365 ProPlus. You also learned how to manage activated installations.
At this point, you should have a good idea of what all goes into planning for and deploying Windows 10 and Office 365 ProPlus.
CHAPTER 2: KEY MICROSOFT CLOUD OFFERINGS
 Welcome to Key Microsoft Cloud Offerings. In this chapter, we are going to take a look at Microsoft Azure, Microsoft 365, and even some other cloud platforms.
Welcome to Key Microsoft Cloud Offerings. In this chapter, we are going to take a look at Microsoft Azure, Microsoft 365, and even some other cloud platforms.
You’ll learn what Microsoft Azure is and about key services that it provides. We’ll take a look at Azure Active Directory, Azure Information Protection, Azure Backup, and the Azure Content Delivery Network. We will also talk a little bit about Azure Key Vault, Multi-Factor Authentication, Azure Virtual Machines, and Azure Virtual Networks.
Next, we will cover Microsoft 365. We are going to talk about what Microsoft 365 is, about some of its key offerings, and how it differs from Office 365. We’ll also look at some of the core benefits of Microsoft 365.
We’ll wrap this chapter up by looking at the similarities among Amazon AWS, Google Cloud, and Microsoft Azure.
By the time we finish this section, you should have a pretty good understanding of what Microsoft Azure brings to the table, what Microsoft 365 brings to the table, and how AWS and Google are similar to Microsoft.
Microsoft Azure
Azure is Microsoft’s cloud computing platform. Organizations use it to deploy and manage applications and services. It’s hosted by a global network of Microsoft managed data centers. Leveraging Microsoft Azure allows organizations to deploy, in days or weeks, solutions that, at one time, took months to deploy.
While Microsoft Azure offers well over 100 different services, some are more important than others.
Azure Active Directory, for example, is used for identity management and access control for cloud applications and resources. You can even synchronize Azure AD with traditional on-prem Active Directory domain controllers. Azure AD also offers single sign-on, or SSO, capabilities that allows you to simplify access to cloud applications for your users by allowing them to login to all apps and resources using a single set of login credentials.
Azure Information Protection, or AIP, is an offering that allows organizations to use encryption, identity, and authorization policies to protect their sensitive information.
Azure Backup can be used to backup machines to the cloud and to restore from the cloud.
The Azure Content Delivery Network allows organizations to provide content to its users, regardless of their location in the world, through a network of global data centers. The purpose of the content delivery network is to allow delivery of this content with minimal latency and increased availability.
Azure Key Vault is used to protect and manage keys, certificates, and other secrets in Azure. These secrets can be protected using hardware security modules, or HSMs.
Multi-Factor Authentication is another key offering available through Azure. It allows you to configure multiple methods of authentication, which, in turn, helps prevent unauthorized access to not only cloud applications, but also to on-prem applications.
Virtual Machines and Virtual Networks are two of the staples of Microsoft Azure. They allow you to create virtual networks within Azure and to deploy Windows servers and Linux servers in Azure, and to connect them to your virtual networks. Your virtual networks can then be connected to on-prem networks through various VPN connections.
To read more about the many different Azure services that are available, visit this URL.
Microsoft 365
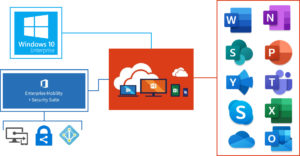 Microsoft 365 is actually a collection of three main products, each of which consists of its own sub-collection of products and services. When you purchase a Microsoft 365 subscription, you get Office 365 Enterprise, Windows 10 Enterprise, and Enterprise Mobility + Security, or EMS.
Microsoft 365 is actually a collection of three main products, each of which consists of its own sub-collection of products and services. When you purchase a Microsoft 365 subscription, you get Office 365 Enterprise, Windows 10 Enterprise, and Enterprise Mobility + Security, or EMS.
Office 365 Enterprise includes Office 365 ProPlus, which is Microsoft’s suite of the latest office apps for PC and Mac. Office 365 ProPlus includes things like Microsoft Word, Excel, PowerPoint, and Outlook. It also includes several online services for email, file storage, collaborations, and meetings.
Windows 10 Enterprise is Microsoft’s flagship desktop operating system (you probably already knew this). It features robust deployment, device management, and application management features.
Enterprise Mobility + Security allows organizations to more effectively manage and protect its users, devices, apps, and data in a mobile centric cloud environment. EMS includes Microsoft InTune, Azure AD Premium, and Azure Rights Management.
Microsoft 365 versus Office 365
The terms “Microsoft 365” and “Office 365” are often used interchangeably.
Office 365 is a productivity suite that bundles several productivity tools into a software-as-a-service model. As I mentioned earlier, Office 365 includes the latest office applications and some other online services.
Microsoft 365, however, is different. It’s actually a larger offering, that includes Office 365 Enterprise, Windows 10 Enterprise, and EMS. You can view Microsoft 365 as an umbrella of offerings, under which Office 365 falls.
Microsoft 365 Benefits
Because it’s an umbrella of services that includes Office 365, Windows 10 Enterprise, and Enterprise Mobility and Security in a single subscription, Microsoft 365 helps organizations in several different areas.
Creativity
The powerful capabilities of Microsoft 365 can be used by users to create slick presentations, mixed-reality experiences, and other high-quality content. With its AI-powered tools, Microsoft 365 also helps organizations turn data into actionable insights.
Teamwork
Microsoft 365, as you would expect, also provides several tools that can be used to facilitate teamwork and collaboration within organizations. A tool like Microsoft Teams, for example, allows users to collaborate in real time. It allows them to chat, hold meetings, and even share files and applications.
Users can leverage Microsoft Outlook to access, email, calendars, contacts, and documents. SharePoint Online is another collaboration tool. It allows users to share things like news, applications, and even resources across the organization by building portals and dynamic sites. OneDrive for Business provides users the ability to securely share files and to track versioning history.
Simplicity
Because Microsoft 365 allows organizations to centrally provision, deploy, and manage all of their devices, whether they are mobile devices or PCs, Microsoft 365 vastly reduces IT complexity and lowers costs. It helps organizations become more agile as a result. Leveraging cloud security allows organizations to improve their security posture, while allowing them to administer their applications, their services, their devices, their data, and their users, all from a single web-based admin portal.
Security
Microsoft 365’s holistic approach to security allows organizations to protect users, devices, applications, and data. Its built-in intelligent security protects organizations against threats and even offers automated remediation of many of those threats.
Other Cloud Solutions
The big three providers, including Azure, AWS, and Google Cloud all offer scalable computing resources on demand. The services are all actually quite similar. However, where they really differ, is in the pricing models and in which services are supported.
AWS and Google Cloud both offer a few different storage plans that can accommodate the hot storage and cold storage requirements of organizations. While the features and pricing may differ from Microsoft’s offerings, the purpose of the offerings remains the same - to reduce costs and to improve access speeds to data.
Each of these providers also offers its own set of analytics tools. That said, the supported technologies and programming models for each differs a bit, depending on the platform. Both AWS and Google also offer development tools that organizations can use to build, deploy, and manage applications - just like Microsoft does.
And last but not least, all three cloud providers offer the basics, which include networking services, content delivery services, management tools, and security features. As you would expect, the tools available from each provider will differ in many ways, including the levels of control that each offer, and the ease-of-use for each tool.
What You’ve Learned
Congratulations! You’ve reached the end of Key Microsoft Cloud Offerings. Let’s review what you’ve learned.
We kicked things off by taking a look at Microsoft Azure. You learned what Microsoft Azure is and about key services that it provides. We covered Azure Active Directory, Azure Information Protection, Azure Backup, and the Azure Content Delivery Network. We also talked a little bit about Azure Key Vault, Multi-Factor Authentication, Azure Virtual Machines, and Azure Virtual Networks.
We then dove into Microsoft 365. You learned what Microsoft 365 is, about some of its key offerings, and how it differs from Office 365. You also learned about the core benefits of Microsoft 365.
We wrapped up by looking at the similarities among Amazon AWS, Google Cloud, and Microsoft Azure.
At this point, you should have a pretty good understanding of what Microsoft Azure brings to the table, what Microsoft 365 brings to the table, and how AWS and Google Cloud are similar to Microsoft.