CHAPTER 5: Unified Endpoint Management
 Welcome to Unified Endpoint Management. In this chapter, we are going to cover unified endpoint management topics.
Welcome to Unified Endpoint Management. In this chapter, we are going to cover unified endpoint management topics.
We will start things off with device management in today’s workplace. You’ll learn about key unified endpoint management concepts and how IT departments can support different devices in the modern workplace.
Next, we’ll cover the many different components of the Enterprise Mobility and Security suite. You’ll learn about Azure AD, SCCM, Azure Information Protection, and much, much more. You’ll learn what each component is and what role each component plays.
Rounding things out, we’ll get into cloud-connected device management, where you’ll learn about the different ways that you can manage cloud-connected devices.
We have quite a bit to get to. So, let’s get started.
Device Management in the Modern Workplace
Unified endpoint management refers to a platform for managing devices and applications. Using Microsoft InTune and System Center Configuration Manager, both of which are parts of Enterprise Mobility and Security within a Microsoft 365 subscription, can help simplify management. Using these products creates an environment that allows end users to use whatever devices and applications they choose, while still offering protection for the organizations data.
The modern workplace presents unique challenges for IT departments because they need to support many different devices that are configured in many different ways. Some users may have Android devices, while others may use iOS smartphones. Yet others may use Windows 10 machines, while others use Macs. In addition to supporting the devices themselves, IT departments need to ensure that these devices all meet the security standards and health standards that are established by the organization. Such devices also need to be configured to support whatever applications and features the organization uses.

Each of these different devices clearly presents different management challenges. For example, users will often use mobile devices and laptops that connect to outside networks through public Wi-Fi access points. Because hackers will often use public access points to capture network traffic and insert malware into a user’s browsing sessions, the fact that mobile devices often connect to unsecured networks like these can impact every user in the organization.
While devices that connect to unsecured networks can be a problem, so can mobile devices that only intermittently connect to the corporate network. This is because tools like Group Policy, which are used to manage devices, usually assume that these devices are always connected to the corporate network. Because they are not, these mobile devices can be difficult to manage with traditional tools.
Users will often connect to the corporate network and access files from central file shares and from SharePoint sites. While these centralized storage locations are often backed up, mobile devices, which include laptops, typically are not. Because these devices aren’t backed up, any data that is created directly on them is not backed up either. If one of these devices is stolen or suffers a serious hardware failure, this locally created data is lost.
 Speaking of lost or stolen devices… Quite often, the cost of replacing a stolen device can far exceed the original cost of the device itself. This is because the organization needs to not only replace the device, but it also needs to configure the device and determine what data was lost or stolen. This all requires time - and time is money.
Speaking of lost or stolen devices… Quite often, the cost of replacing a stolen device can far exceed the original cost of the device itself. This is because the organization needs to not only replace the device, but it also needs to configure the device and determine what data was lost or stolen. This all requires time - and time is money.
Another struggle that IT departments deal with are devices that have been compromised and then connected to the corporate network. This is a problem because a device that’s been infected with malware cannot only steal data, but also spread the malware to other devices in the organization. Because of this, mobile devices must be treated as potential threats, and precautions must be taken to prevent attacks and to prevent leaks.
Personal devices also pose significant challenges to most organizations because those organizations need to decide if they wish to allow users to access corporate apps and data from their personal devices. This requires organizations to implement mobile device support policies. Organizations need to decide whether they will allow user owned devices to access corporate applications and data or if they will only allow this access only if the owner of the device allows the organization to manage the device. Organizations also need to decide what actions can be taken to protect any corporate data that is stored on the device. In the event the device is lost or if the user leaves the company.
The proliferation of BYOD in today’s modern workplace has made work easier for end users, but as you can see, it also presents significant challenges to IT departments.
Enterprise Mobility + Security Components
Enterprise Mobility + Security is a tool that you can use to manage all devices within your organization. It’s intended to help organizations protect and secure their environments. The EMS suite of products comes included with Microsoft 365 E3 and E5 plans.
The table below provides a summary of what is included.
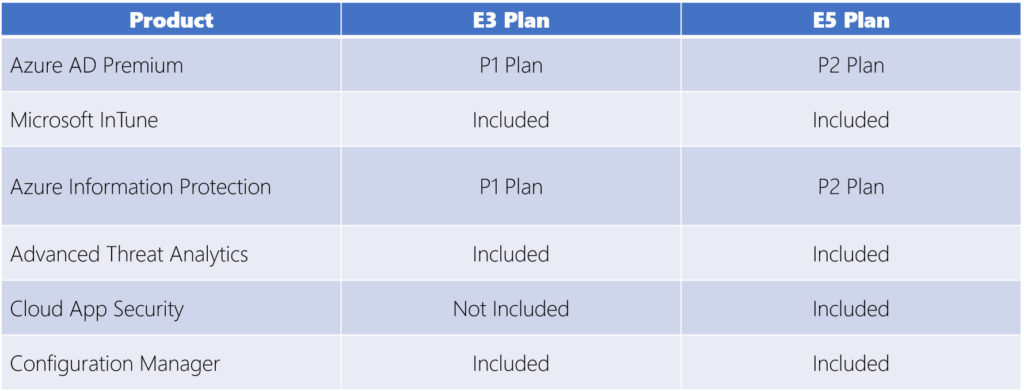
Azure AD Premium is a central identity store. All applications in EMS and in Microsoft 365 use this identity store. There are three different levels of Azure AD premium. They include Basic, P1, and P2. The Basic level includes basic features that can be used to facilitate endpoint management. However, the P1 and P2 plans come with additional features, including Self-Service Password Reset, Write-Back from Azure AD to On-Prem Active Directory, and Microsoft Azure MFA for Cloud and On-Prem Apps. Other features that come with the P1 and P2 plans include Conditional Access Based on Group, Location, and Device, and in the case of P2, Conditional Access Based on Sign-In or User Risk.
Another component to EMS, is InTune. This cloud-based enterprise mobility management service protects corporate data while facilitating end-user productivity. Identity and access control are achieved through its integration with Azure AD, while data protection is achieved through its integration with Azure Information Protection. You can also use InTune to enforce security policies, deploy applications, and even remotely wipe devices when they are lost or stolen.
System Center Configuration Manager, or SCCM, is an on-prem product that organizations can use to manage Windows PCs, Mac OS PCs, and servers. This product allows organizations to customize application management, OS deployments, and even device compliance.
Azure Information Protection, or AIP, is a component of EMS that organizations can use to encrypt documents and to enforce policies on how those documents can be used.
Microsoft Advanced Threat Analytics is another component of EMS. With Advanced Threat Analytics, organizations can detect suspicious activities and malicious attacks. This allows them to adapt to the ever-changing landscape of cybersecurity threats. Microsoft Advanced Threat Analytics also helps organizations reduce false positives.
Cloud App Security is an add-on that can be combined with your organizations Microsoft 365 subscription. It provides visibility into cloud apps and services, while also providing analytics that you can use to identify and mitigate security threats.
Cloud App Security takes data that’s been collected from your organization’s firewalls and proxy servers and uses it to track cloud application usage. Using Cloud App Security, you can identify unauthorized applications that are in use and that might be a threat to your organization. It also allows organizations to identify unusual usage patterns.
Microsoft Identity Manager essentially combines Microsoft’s identity and access management solutions together. It takes different on-prem authentication stores, including AD, Oracle, LDAP, and others, and bridges them with Azure AD to provide a consistent identity experience for on-prem applications as well as SaaS solutions.
Azure Advanced Threat Protection, or ATP, is a cloud-based solution that allows organizations to not only identify and detect threats and malicious activities but to also investigate them as well. You can use Azure Advanced Threat Protection to identify suspicious user and device activity and to analyze threat intelligence from the cloud, and on-prem. Azure Advanced Threat Protection helps protect user identities and credentials that are stored in Active Directory and allows you to view attack information on a simple timeline. This allows for faster triage.
As you can see, Enterprise Mobility and Security offers quite a few tools that you can use to manage security and devices within your organization.
Cloud-Connected Device Management
If your organization already uses Configuration Manager on-prem to manage devices, it can be connected with the cloud-based InTune management system through the co-management function of Configuration Manager. When you connect the two using the co-management function, you can manage your Windows 10 devices with both Configuration Manager and Microsoft InTune at the same time. What this does is add InTune functionality to your device management solution.
Connecting Configuration Manager with the cloud-based InTune management system provides several benefits over using Configuration Manager alone. For example, with this cloud connected system, you can use conditional access to make sure that only trusted users can access corporate resources from trusted devices, using trusted apps.
You can also manage all registered devices every time they connect, regardless of where they are. These remote actions allow you to wipe such devices when they are lost or stolen. You can also rename and restart devices remotely, and even perform factory resets on Windows devices.
While Configuration Manager can monitor the health of your devices while they are connected to the network, Microsoft InTune can communicate with co-managed devices, and monitor their health, even when they are not connected to the network - and it can report on the health of those clients.
To ensure that new devices that are added to your network get configured the same way as existing devices, you can use co-management and Windows 10 Autopilot together. When you use Windows 10 Autopilot and co-management together, you can take advantage of the Windows 10 provisioning model, which helps eliminate the need to deal with creating and updating custom operating system images.
Leveraging Azure Active Directory lets you link users, devices, and applications from both cloud and on-prem environments. When you register your organizations devices to Azure AD, you can improve security while increasing productivity of your end users. Registering devices in Azure AD provides the ability to co-manage them and to leverage device-based conditional access. It also allows you to offer single sign-on to cloud resources, automatic device licensing, self-service functionality, Windows Hello for Business, and enterprise state roaming.
So, with that said, if you have an existing on-prem Configuration Manager infrastructure, connecting it with a cloud-based InTune management system through the co-management function allows you to reap significant benefits.
What You’ve Learned
Congratulations! You've reached the end of Unified Endpoint Management. Let's review what you've learned.
Throughout this chapter, you learned about several unified endpoint management topics.
We started things off with device management in the modern workplace. You learned about key unified endpoint management concepts and how IT departments can support different devices in the modern workplace.
Next, we covered the many different components of the Enterprise Mobility and Security suite. You learned about Azure AD, SCCM, Azure Information Protection, and much, much more. You also learned what each component is and what role each component plays.
Rounding things out, looked at cloud-connected device management, where you learned about the different ways that you can manage cloud-connected devices.
At this point, you should have a pretty good understanding of unified endpoint management options in Microsoft 365.
Prefer the PDF version? No problem.
Click here to download the full 89-page PDF version of this guide for just $2.99.
As an added BONUS, I've included 30 Microsoft 365 practice questions in the PDF version.
Prefer the full 3-hour online course? Click here to enroll in the full course.
About the author